Mobile devices are being used by 5.19 billion individuals to complete a variety of functions. Mobile users are simplifying their lives by using smart gadgets to do anything from pay bills to check emails, purchase groceries to send instant messages. Because of the growing need for mobile applications, businesses of all sizes are building mobile apps to meet the ever-increasing demands of their clients.
Security and data breaches in mobile applications are not only expensive in terms of money, but also in terms of lost customer and staff confidence. In the event of a breach, the targeted organization is always held accountable since customers trust them to protect their sensitive data.
The security of mobile apps is a shifting objective. The need for improved functionality and features, as well as the quick distribution of software upgrades, frequently comes at the price of mobile security. The expanding mobile app security threats, particularly to avoid data breaches, are one of the primary issues for mobile app development.
As technology progresses, it has gotten easier not just to design and deploy apps, but also to breach a mobile application's security, since developers continue to write risky code. Some attackers may attempt to break a mobile app to learn more about the special features and other information about your mobile app. Others may do it to compromise backend services.
But, before we start to find out the measures to maintain mobile app security, let’s understand it conceptually.
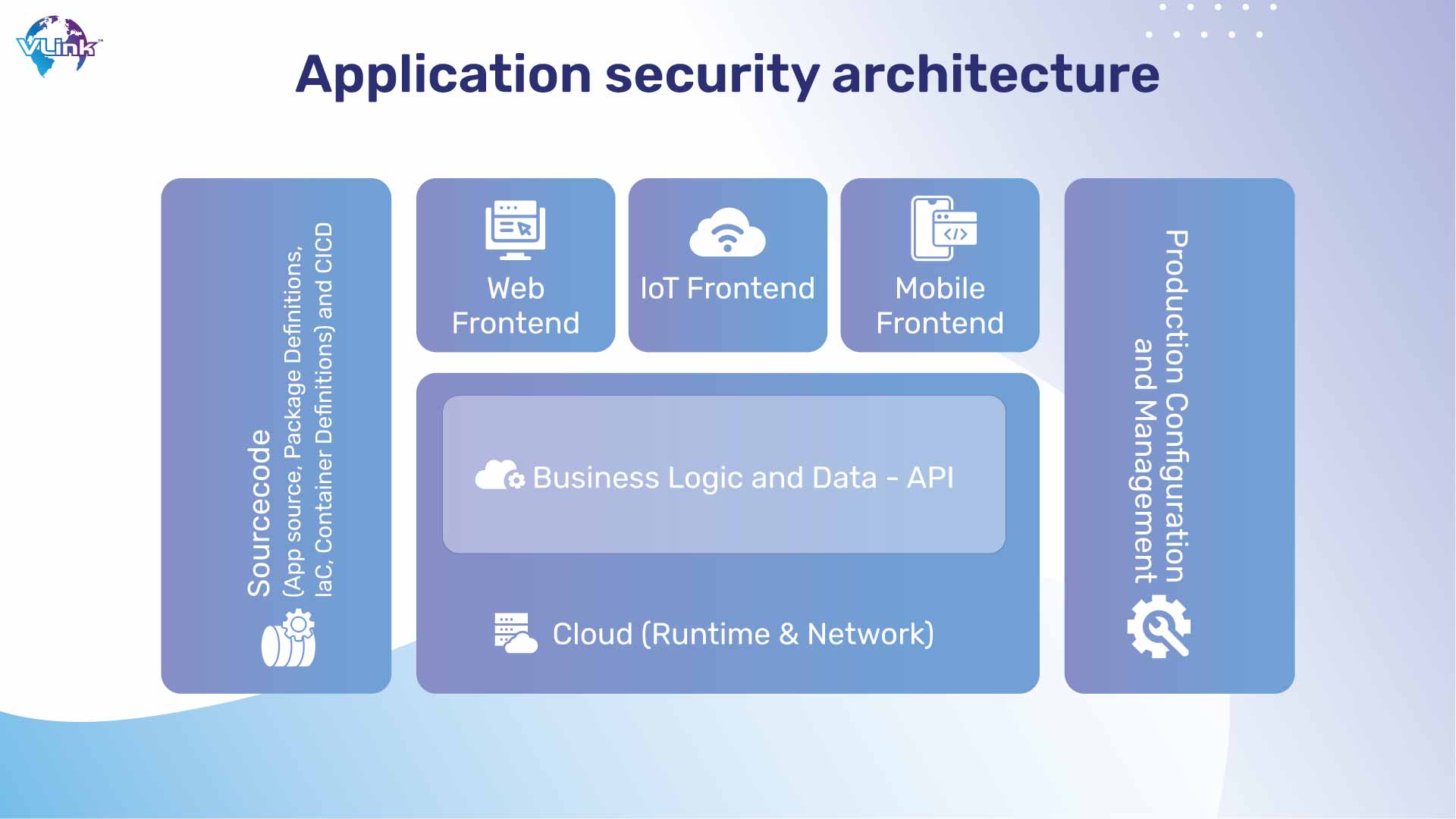
Understanding mobile app security
Most digital actions undertaken by clients are now performed on mobile app development rather than traditional desktop programs, which is a new high. In 2022, mobile applications will account for 59% of users' active media consumption on mobile devices.
These applications have access to a large amount of user information, the majority of which is sensitive information that must be protected from unauthorized access. Customers usually rely on businesses and trust that they would test their applications for security features before making them available to the public. Nonetheless, IBM conducted tests that yielded some astonishing results.
The numbers are enough motivating for hackers to target security holes in mobile applications, and they aim to employ one or more of the following approaches from unprotected code: As a result, mobile app security is a critical component for any organization seeking to protect its customers' identities and sensitive data.
According to NowSecure's examination of over 400,000 mobile apps, 25% of all mobile apps contain at least one high-risk security issue. These applications were three times more likely than other apps to lose their users' passwords.
Companies in the information, media, financial services, publishing, and retail sectors are increasingly worried about their consumers and company data. They are prepared to raise their mobile security budget to secure data and avoid harmful assaults.
Crucial practices to implement mobile app security
1. Use Secure Network Communication
Sensitive data can be intercepted during internet transmission and used fraudulently or stolen by bad actors. It is crucial to employ secure protocols to encrypt the data in transit to avoid this. This makes sure that even if the data is intercepted, no one who doesn't have the encryption key will be able to read it.
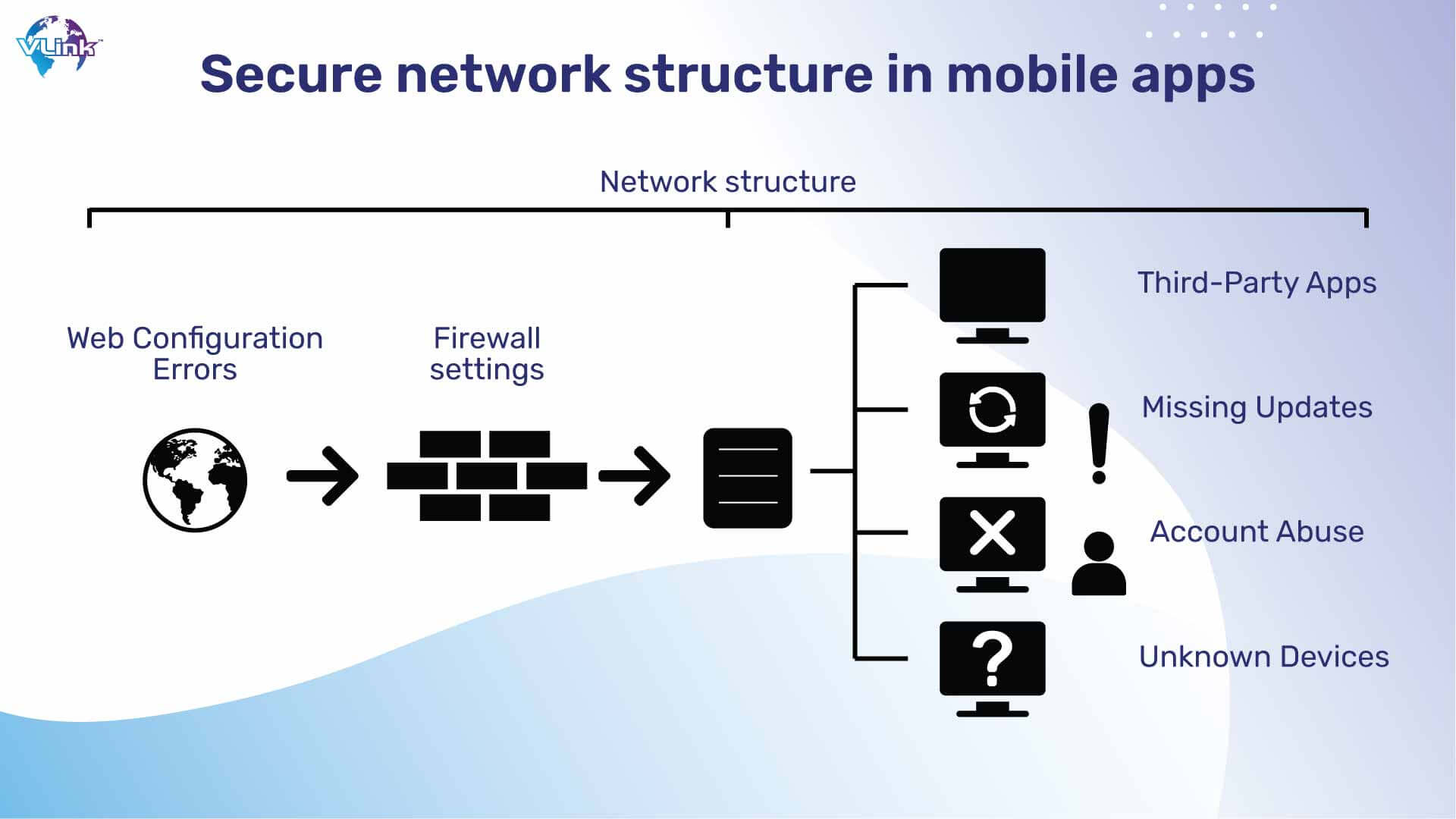
Utilizing secure network connectivity also implies that the program shouldn't save private data on its own servers. Data ought to be kept on the server instead, where data may be secured by extra security measures like firewalls and intrusion detection systems. The important data will be protected in this fashion even if the app is hacked.
2- Minimizing lack of Input Validation
Input validation is the criteria to analyze the input data to make sure it is correctly formatted, avoiding incorrect data from potentially containing malicious code or leading to app malfunction.
When a mobile application does not properly validate input, it exposes the program to potential attackers who might insert fraudulent data input and get access to critical information.
Programming methods that make it easier to enforce data accuracy, such as:
- Minimum and maximum value range checks for dates and numerical parameters as well as length checks for strings, may be used to implement input validation.
- XML Schema and JSON Schema input validation
- Checking the minimum and maximum length of dates and numerical parameters, as well as the minimum and maximum value range for strings.
- Regular expressions spanning the complete input string rather than utilizing the "any character" wildcard for any other structured data.
- An array of acceptable values for short strings of parameters (such hours or days);
Alternately, allowing only known good rather than just rejecting known bad is a more effective technique to stop attacks brought on by insufficient input validation. If done correctly, this can set up stricter restrictions.
A powerful input data validation pattern based on regular expressions should be able to be built and implemented by the mobile app developer if the input data is structured, such as social security numbers, dates, emails, zip codes, etc.
3- Client Code Security
In mobile apps, code security vulnerabilities are rather typical. You can use automated, outside tools to do fuzzing or static analysis in place of manual code reviews, which can take a significant amount of time to find many of these errors.
These tools may spot security problems such data storage security flaws, injection problems, and inadequate encryption. To detect security issues where automation falls short, you still require manual inspection in addition to automated technologies.
Consistently use secure coding techniques to prevent susceptible code. Make careful to check that the length of the incoming buffer data does not exceed the length of the target buffer when employing buffers.
Utilize automated static analysis methods to find memory leaks and buffer overflows. Make careful to pay memory leaks and buffer overflows more attention than other code quality concerns since they frequently result in greater mobile security threats and may be readily exploited.
4- Optimizing Poor Encryption
Encryption is the act of transforming data into an encrypted format that can only be decoded with a private decryption key. Attackers can access data far more easily if devices and data are not securely secured.
Even the greatest encryption methods can fail if the keys are not handled properly, even though developers frequently use strong encryption. For instance, putting the keys in files or databases that are not secure and are accessible to other users.
One of the most frequent failures we observe is this. Attackers pursue the keys rather than attempting to crack the encryption method because it is too difficult. Unfortunately, poor key management is a significant problem.
Custom encryption algorithms or protocols are another way mobile developers handle encryption incorrectly. These encryption methods are frequently less secure than other cutting-edge ones that the security industry has access to. Additionally, employing RC2, MD5, MD4, and SHA1 encryption methods that are weak or vulnerable might result in attacks.
5- Insecure Data Storage
Your mobile app may have insecure data storage in a variety of locations, including binary data stores, SQL databases, cookie stores, and more. You run the risk of having your data compromised if you employ an unsecured data storage because of problems with jailbroken devices, frameworks, or other assaults.
If a mobile app's security measures are not properly implemented, such as using subpar encryption libraries that can be gotten around by jailbreaking or rooting the device, attackers can simply defeat them. An attacker who gets access to a device or database can alter a legitimate program to extract data for their own systems.
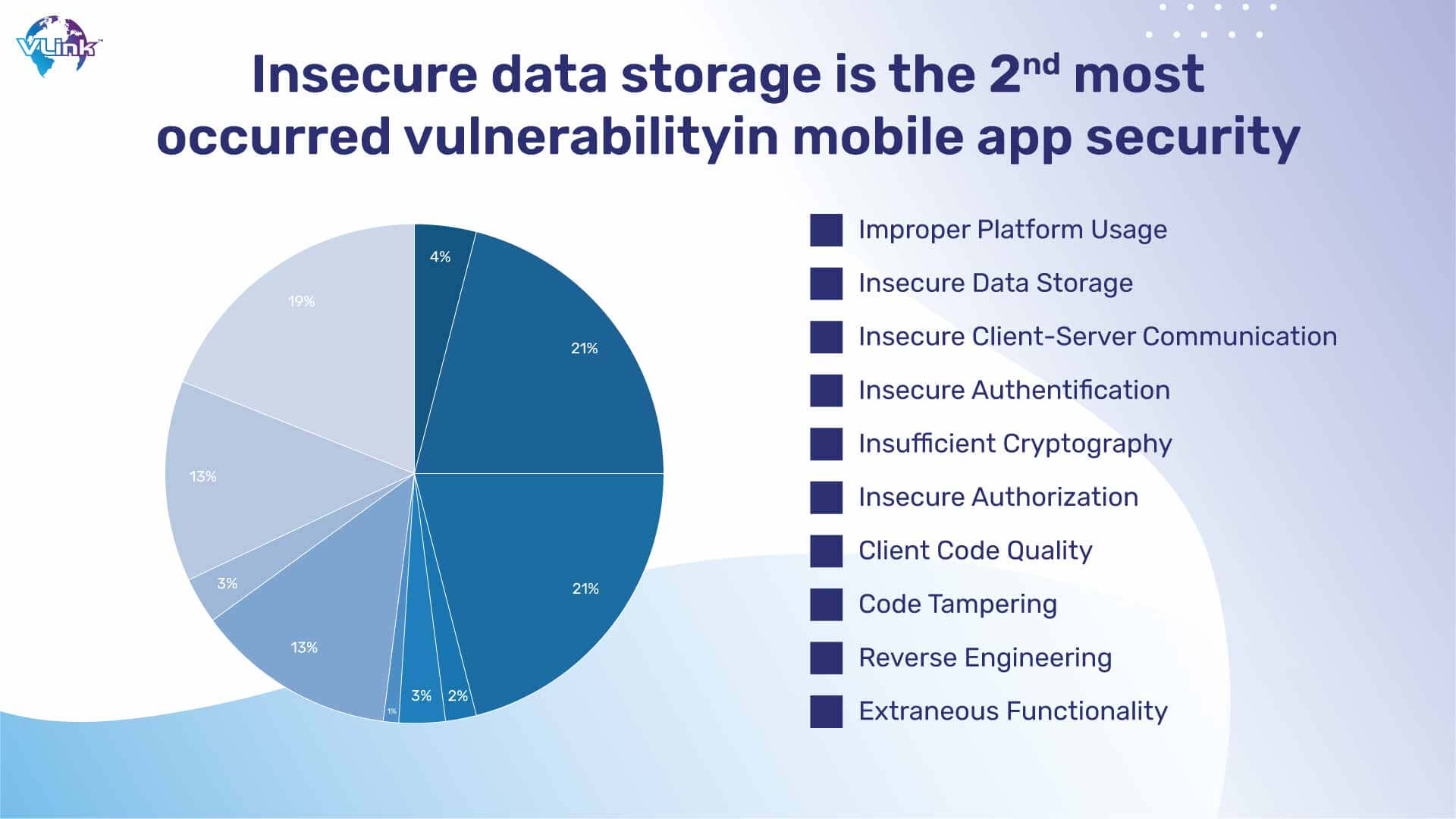
Companies need to manage the lack of authorization while accessing the data through different resources in a mobile app. And that’s where issues occur. All storage information should be placed and allotted to a certain level of security.
Also Read: Top Mobile App Development Trends To Follow
6- Controlling insufficient authentication & authorization
Attackers can utilize the mobile application or the backend server it uses to conduct functionality while remaining anonymous if authentication procedures are missing or inadequate.
In that user not need to be always online during their session, mobile apps' authentication requirements might differ from those of standard web applications.
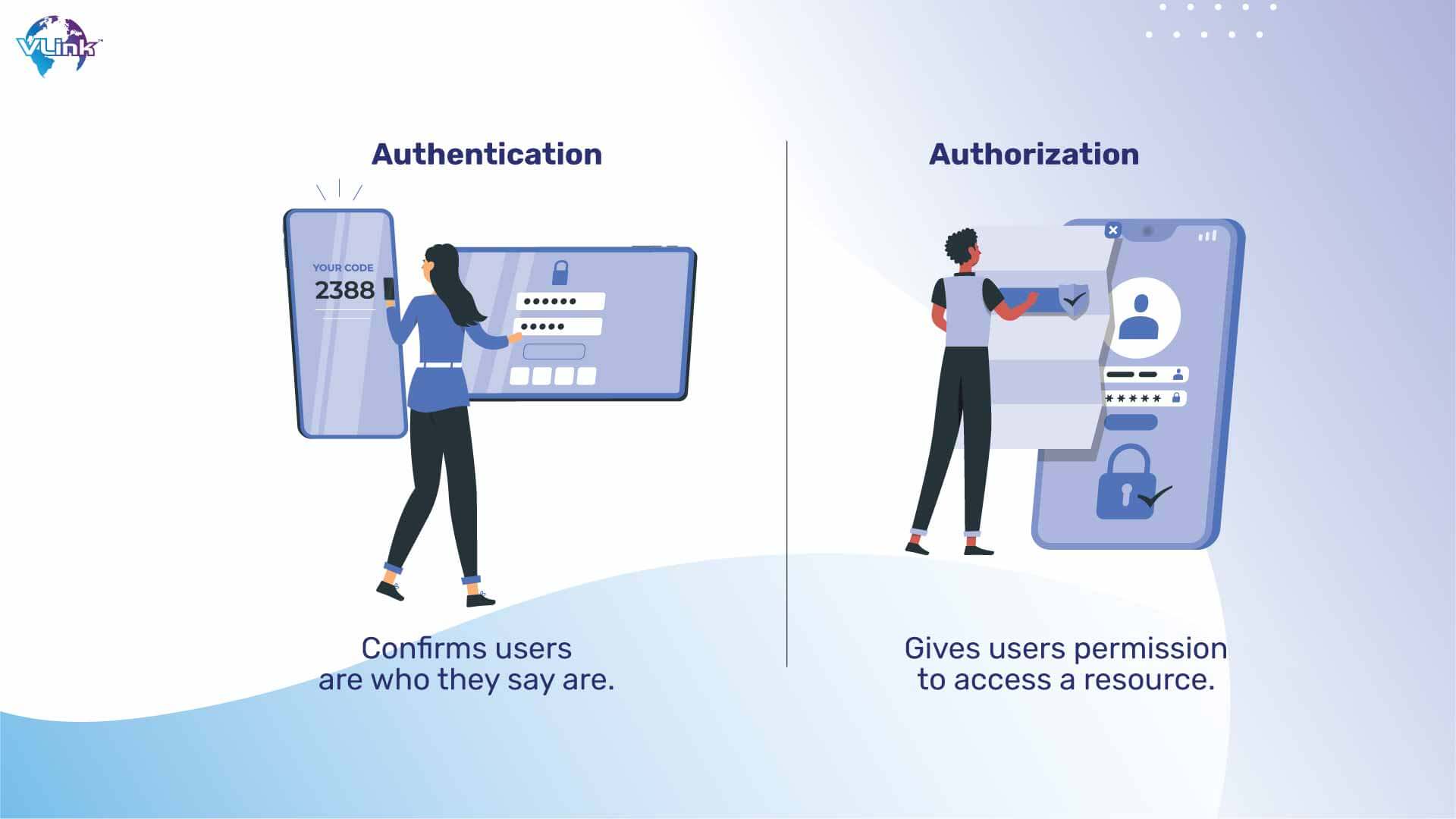
You can boost mobile security in several ways by implementing correct authentication and authorization:
- Make sure to check the authentication factor is working or enabled in mobile app. If it is working properly then data can only be loaded once the authentication is successful.
- If client-side data storage is necessary, safeguard your data using encryption and securely utilize the user's credentials.
- Verify the responsibilities and permissions of authorized users exclusively utilizing data from backend systems to develop strong authorization mechanisms.
- A user's identity should be verified via multi-factor authentication. One-time passwords, security questions, etc. are all options.
It's probable that offline authentication is necessary for mobile apps' uptime needs. When developing authentication systems, developers should take security concerns into account when using this technique of offline user identity authentication.
7- Reverse Engineering
An attacker can find more effective ways to attack your application if they can read your code. Reverse engineering is a technique that may be used to alter the source code, reveal the encryption techniques in use, and more.
Therefore, the code you wrote for your mobile app poses a serious security risk and might be utilized against you. Limiting client-side functionality and exposing more through server-side web services are efficient ways to stop reverse engineering of mobile apps.
Once functionality has been reduced to the absolute minimum required, the code base is obfuscated using commercial obfuscators.
Avoid keeping API keys in shared resource files, assets, or any other location that is open to outside access. Protect your mobile app's API key by using NDK or public/private key exchange.
How does VLink maintain mobile app security?
VLink’s technique for implementing and verifying the security of mobile applications is based on our more than ten years of security experience. To detect vulnerabilities in mobile apps, we employ specialized static and dynamic analysis techniques created especially for the mobile environment, as well as manual verification and analysis.
These tools aid in the identification of problems that can be brought on by a confluence of application code and platform version since they are often updated and tested against new versions of the underlying mobile platforms.
Our testing checks for problems with the back-end services that the application uses in addition to looking for flaws in the app itself. We make sure that all facets of the application are tested by concentrating on both the app and its back-end services.
Frequently Asked Questions
Authentication, authorization, encryption, logging, and application security testing are a few examples of several kinds of application security features. Mobile app security experts can build customized codes to minimize the security flaws.
Data belonging to your customers is kept safe and secure by securely developing your mobile app. Malicious actors could be able to access client information without sufficient security safeguards in place, or even use the app to target other systems.
The implementation of mobile app security practices usually takes place at the end of development and during the testing phase. Every system, project, or application that is created or upgraded to satisfy a business requirement must consider and handle the security obligations set out in the Secure Systems Development Lifecycle (SSDLC).












