The industry undergoes transformations each year. As cybersecurity threats advance, defensive tools also evolve, adapting to safeguard progressively complex networks.
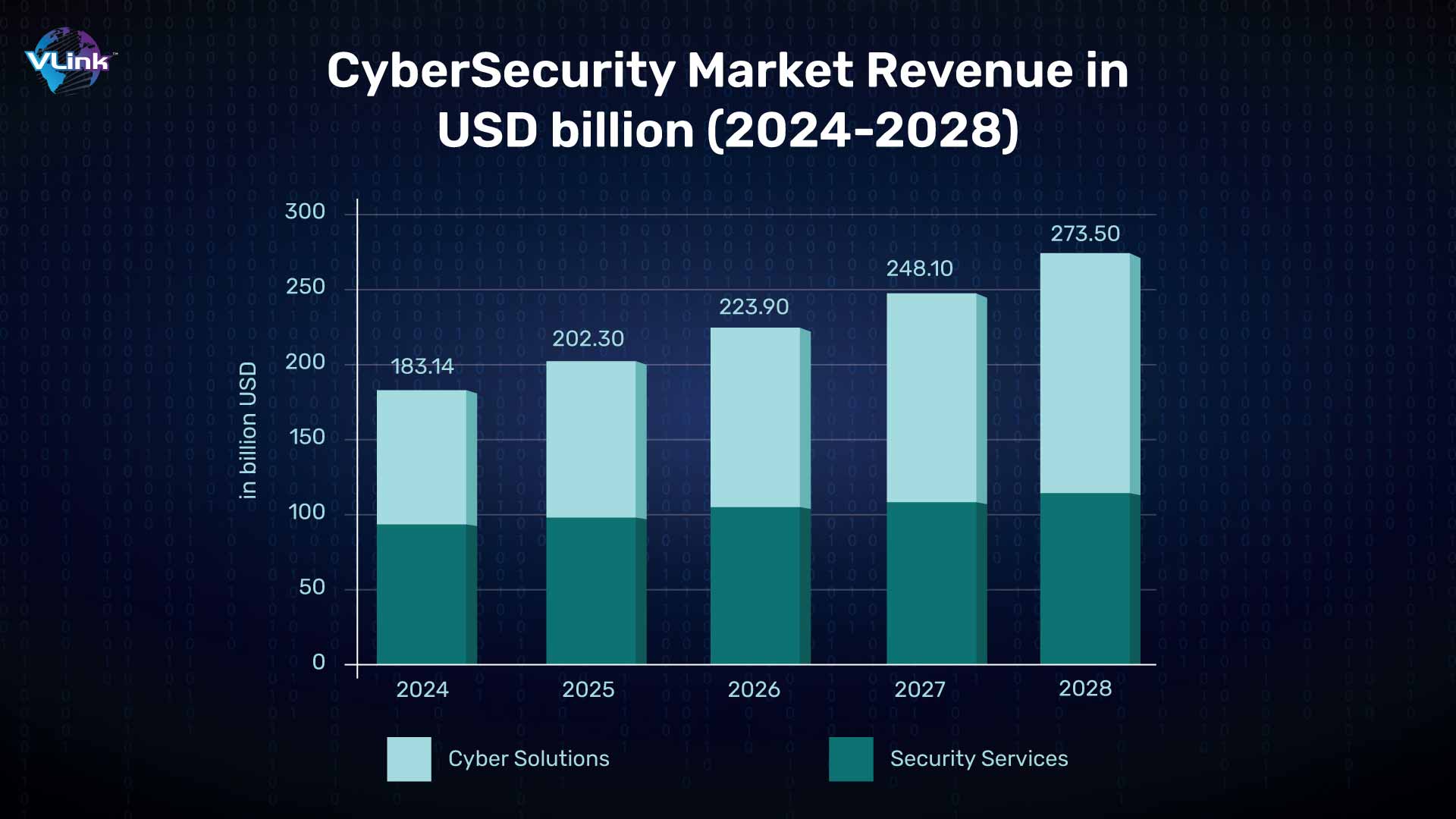
Cybersecurity market revenue is predicted to reach USD 183.10 billion in 2024 and USD 273.60 billion by 2028, with a CAGR of 10.56%.
 A growing number of cybersecurity threats have many areas on high alert, including corporations, governments, school systems, utilities, and financial institutions.
A growing number of cybersecurity threats have many areas on high alert, including corporations, governments, school systems, utilities, and financial institutions.
From sophisticated state-sponsored attacks to social engineering threats, cybercriminals or hackers are using increasingly cunning tactics to exploit security vulnerabilities. Posing risks from financial loss to reputational harm, in this blog, we will explore the eight most significant cybersecurity threats and cybersecurity trends and tips to deal with them.
8 Biggest Cybersecurity Threats in 2024
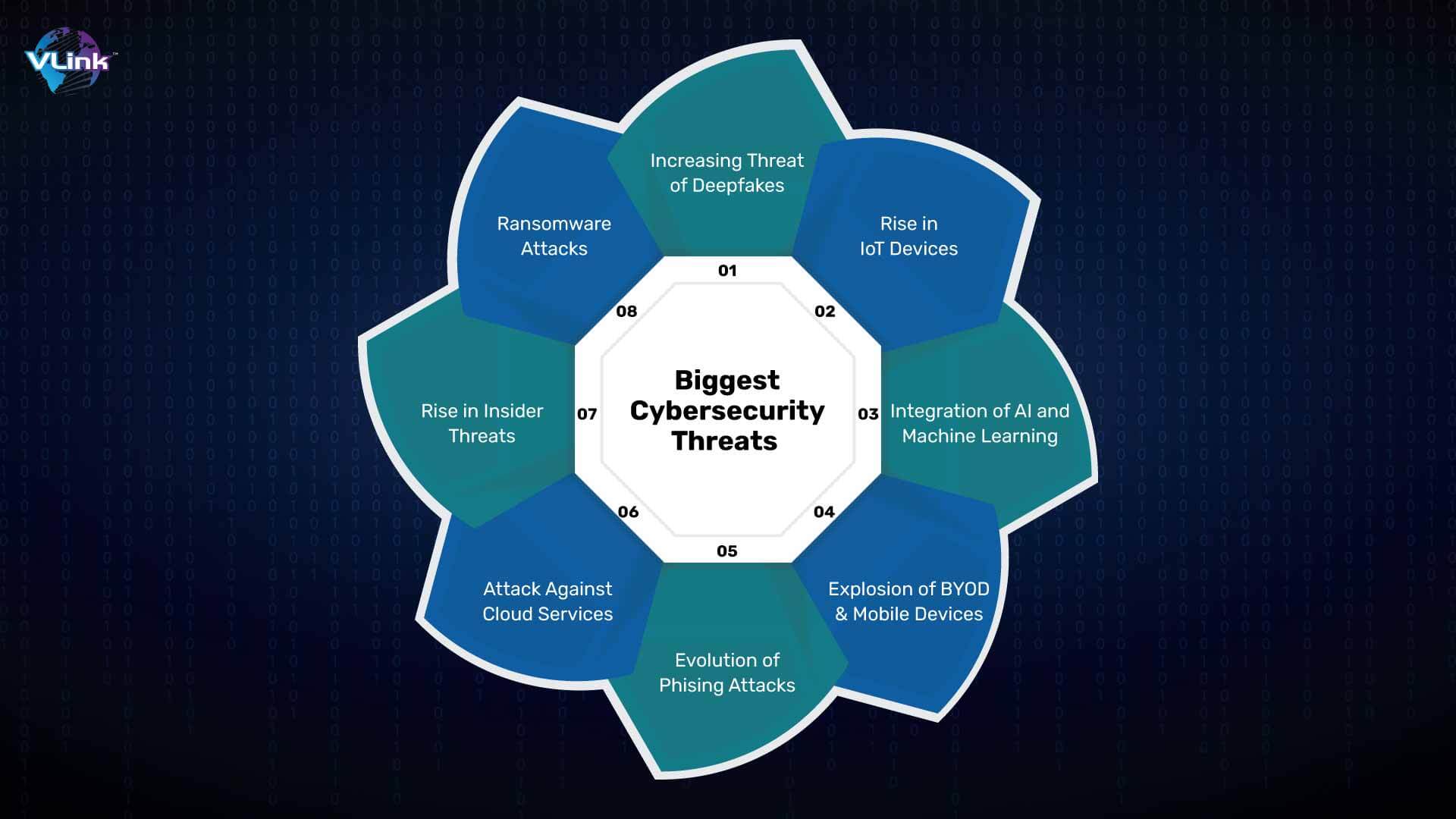
#1 - Increasing Threat of Deepfakes
In the era of plentiful online content, the emergence of deepfake technology presents the biggest cybersecurity threats in 2024 & beyond. Deepfake is a manipulating video, audio, and image that blurs the line between fake and real.
Deepfakes is used for financial scahms, social engineering threats, impersonating individuals, and spreading disinformation. Even politicians (Joe Biden) or celebrities (Taylor Swift) are also impersonated by deep fakes.
As the threat of deepfakes grows, businesses will need to invest in top AI deepfake detector tools and strategies to protect their reputation and data integrity.
The AI deepfake detection tool market's estimated value will reach USD 1339.40 Million in 2024. It's predicted to surpass USD 5708.30 Million by 2034, securing a 15.60% CAGR.
#2 - Rise in IoT Devices
The Internet of Things (IoT) comes at the 2nd number on our list of top 10 cybersecurity threats in 2024 & beyond.
IoT is growing at an exponential rate, with devices becoming increasingly integrated into our daily lives. From smart homes and smartwatches to baby monitors and smart lights, hackers use all smart devices surrounding you to access your device and steal your sensitive data.
As IoT devices become more popular, so do cybersecurity threats. Their diversity, prevalence, and interconnected nature make them the primary targets for cyber-attacks.
The number of connected devices is anticipated to surpass 14.4 billion by 2024. IoT Analytics claims that by 2025, the count will exceed 27 billion gadgets online.
As a result, hackers will have ample opportunity to exploit compromised data security for malicious purposes.
So, there is a primary focus on improving the cybersecurity in the age of IoT devices and their connected networks.
#3 - AI and Machine Learning Attacks
There is no need to mention that Artificial Intelligence (AI) and Machine Learning (ML) can be both a boon and a bane at the same time.
In cybersecurity, AI can be a boon if it is used as a threat. On the other hand, it can be a bane if it is used as a solution.
AI's advanced data analysis capabilities allow for the identification and prediction of cyber threats, enhancing early detection systems. ML algorithms are evolving to recognize better and respond to new threats, improving defensive measures over time.
Machine learning and AI can be a game changers in online retailers when it comes to threat detection and prevention. Anticipate the emergence of AI algorithms offering real-time threat analysis in 2024, facilitating faster and more precise responses to cyber incidents.
AI in Cybersecurity Market size is expected to reach USD 60.6 Billion by 2028 from USD 22.4 Billion in 2023 to grow at a CAGR of 21.9%
Cybersecurity professionals will harness the power of machine learning and AI development services to stay one step ahead of cyber threats.
#4 - Explosion of BYOD & Mobile Devices
The Bring Your Own Device (BYOD) trend continues to gain momentum. During remote work, employees use their personal devices to complete tasks. Along with flexibility and convenience, this approach also poses cybersecurity threats.
This makes it clear that mobile devices are becoming increasingly integral to both personal and professional life. This makes mobiles attractive targets for cyber threats.
In 2024 and beyond, we will witness a continued explosion of BYOD and mobile device usage. Use robust mobile security solutions to protect your data.
If you want to secure sensitive professional data on these devices, organizations need to implement robust mobile device management (MDM) solutions and enforce security policies.
#5 - Evolution of Phishing Attacks
A phishing threat is a type of social engineering attack that targets users' login and credit card details. It includes the use of fraudulent emails or sites that appear legal but are fake to steal sensitive information. Even a successful phishing attempt can lead to severe financial and personal damage.
Around 36% of all data breaches involve phishing. Officially, Google released a statement explaining how it blocks more than 100 million phishing emails daily.
#6 - Attack Against Cloud Services
From large to small, businesses are using cloud managed infrastructure services to store their user-sensitive information. The benefits are clear: faster time to market, enhanced productivity, minimized costs, and improved flexibility.
Unfortunately, the increasing popularity of cloud services comes with many cloud-based threats. Reduced visibility and control, misconfigured cloud storage and settings, vulnerable cloud applications, incomplete data deletion, compliance issues, and migration concerns will continue to impact your businesses. Even leading companies like Microsoft that practice strict cybersecurity protocols face cloud threats.
To protect your cloud services from these attacks, you need to maintain many considerations for cloud applications and data security. In addition, you can implement a streamlined cloud governance model to accelerate your security response capabilities.
#7 - Rise in Insider Threats
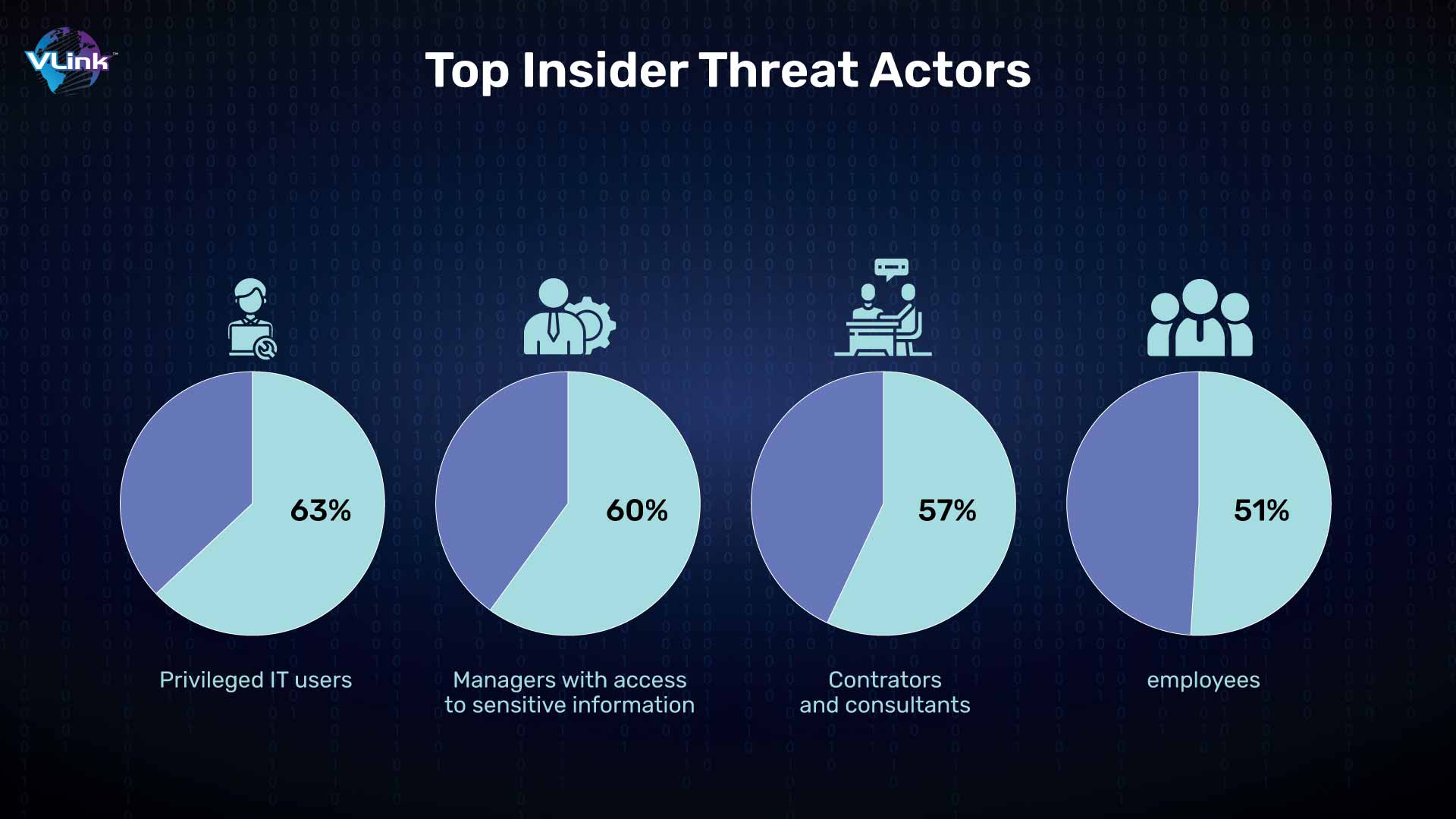
Most of the company's cybersecurity challenges come from outside. But there are times when the attacks come from inside. According to many surveys, most of the time, companies' employees hack their data.
It could result in significant losses for the organization's finances and reputation.
In the United States, the most common type of insider threats includes 62% data exfiltration, 19% privilege misuse, 9.5% data aggregation/snooping, 5.1% infrastructure sabotage and 0.6% account sharing.
It would help if you used insider threat protection to protect your business's confidential data. The global insider threat protection market is projected to grow at USD 13.69 billion by 2030, with a CAGR of 17.4% from 2023 to 2030.
Monitoring both incoming and outgoing data and traffic within the network presents a practical solution for mitigating these threats to computer security. The risk of insider attacks can be reduced by implementing firewall devices to direct data through a centralized server or by restricting file access based on job responsibilities.
#8 - Ransomware Attacks
Ransomware is a constantly evolving cyber threat in today's digital world. Cybercriminals or hackers are continually improving their strategies to increase their profits.
Ransomware attacks are expected to become even more sophisticated in 2024, targeting both individuals and organizations. In 2023, over 72% of businesses globally were affected by ransomware attacks.
The Ransomware Protection Market is forecast to reach USD 24.12 billion by 2025, having grown at a CAGR of 14.87% from 2020 to 2025.
A robust backup and recovery strategy stands as the most effective defense against ransomware. Consistently backing up data, raising employee awareness about phishing risks, and deploying efficient security measures are crucial components.
How to Deal with Cybersecurity Threats in 2024 & Beyond
As we can see, the cybersecurity challenges of 2024 are complex and ever-changing. Here are a few tips on how to deal with them.
- Maintain a robust security approach: It includes having updated security software, strong passwords and a multi-layered strategy.
- Stay informed about the latest threats: Cybercriminals constantly devise new ways to attack. So, it's essential to be aware of the latest cyber threats and their solutions.
- Educate your employees: Employees are often the most vulnerable to security threats. Ensure they stay up to date about the latest threats and understand how to safeguard themselves.
- Have a solid plan against cyber-attacks: If you want to protect your business from future threats, it's crucial to have a prepared plan for a swift and efficient response.
In addition, here are some additional tips for dealing with the cybersecurity threats of 2024.
- Use a password manager: It allows you to create and store strong, unique passwords for all your online accounts.
- Be careful what you click on and what attachments you open: Phishing emails and malicious websites are common ways for cybercriminals to access your systems.
- Ensure your software remains current: Updates frequently contain security patches designed to shield you from identified vulnerabilities.
- Use a firewall: It protects desktops and devices from unauthorized access.
- Regularly back up your data: In the event of malware infection or data theft, having a backup can facilitate data recovery.
By following these tips, you can help protect your business and yourself from cybersecurity threats in 2024 & beyond.
Top 5 Cybersecurity Software for 2024 & Beyond

Sprinto - Best for companies in highly regulated industries
Sprinto is a simple yet powerful automated compliance management information security platform for cloud-based companies.
It smoothly integrates with your cloud configuration to unify risk, map controls at the entity level, and conducts fully automated checks. This cybersecurity software goes above and beyond to initiate remediation, collect evidence, and ensure compliance—all in real time.
Regulatory standards are GDPR, HIPAA, SOC 2, ISO 27001 and 27017, CIS, NIST, CCPA, PCI-DSS, CSA Star, OFDSS, and FFCRA.
Standout Features and Integration of Sprinto:
- Audit success portal
- Dr. Sprinto's mobile device management (MDM) system
- Pre-built integration for AWS, Google Cloud, Azure, ClickUp, GitHub, GitLab, Bitbucket, Jira, Asana, Office 365, and Heroku
- Free demo available
- From $8,000/year
- Rating: 5/5
Pros & Cons of Sprinto Cybersecurity Software:
Pros | Cons |
Streamline auditing process | Relatively steep learning curve |
Robust compliance automation |
|
Responsive customer support |
|
Dynatrace - Best for security applications
Dynatrace is another best cybersecurity software that provides cloud-based monitoring, observability, automation and data analytics solutions. Companies can use this software for their infrastructure and applications.
Key Features and Integration of Dynatrace Cybersecurity Software
- End-to-end infrastructure observability
- APM, distributed tracing, and profiling
- Security protection
- Deliver flawless digital experiences with real-user
- Intelligent and cloud ecosystem automations
Pre-built integration for GitLab, Google Cloud, AWS, Azure, Jenkins, Docker, Kubernetes, JFrog, PagerDuty, and LaunchDarkly
- 15 days free trial
- From $0.08/8 GB/Hour
- Rating: 4.5/5
Pros and cons of Dynatrace cybersecurity software:
Pros | Cons |
Easy to deploy | Only for enterprise applications |
Makes debugging easier | Bad customer support |
Robust software monitoring feature |
|
Azure Sphere - Best for IoT devices
Azure Sphere is a platform for internet-connected devices that you can use to maintain security throughout your development cycle.
Key Features & Integrations for Azure Cybersecurity Software:
- Protect smart devices from chip to cloud
- Deploy updates and maintain device operations
- Accelerate time to market
- Develop secured Internet of Things solutions
- Native integration for Visual Studio and Azure
- Pre-built integration for AWS and Google Cloud
- Free demo available
- From $8.95
- Rating: 4/5
Pros & Cons of Azure Sphere:
Pros | Cons |
Development kit for IoT devices | Limited hardware options |
Integrates with public and private clouds |
|
One-time purchase provides lifetime updates |
|
NetScout - Best DDoS Protection Features
NetScout is an enterprise network visibility cybersecurity software. It provides real-time insights for security, performance, and availability to deliver a seamless user experience.
Key Features & Integration of NetScout:
- Mission Critical Application
- DDoS Attack Protection
- FTTx Network Monitoring
- Accelerated Security Response
Pre-built integration for ServiceNow, AWS, Azure, Google Cloud, F5, Palo Alto Networks, Panorama, Cortex XSOAR, Splunk, and RedHat OpenShift.
- Free demo available
- Pricing upon request
- Rating: 4.5/5
Pros & Cons of NetScout:
Pros | Cons |
Protects both apps and networks | Overwhelming UI |
Scalable | Difficult to setup |
Robust DDoS prevention features |
|
Amazon CloudWatch - Best for AWS
Amazon CloudWatch is a cybersecurity software that observes, monitors resources and applications on AWS, on premises and on other clouds.
Key Features & Integration of Amazon CloudWatch:
- Identify your data with end-to-end observability
- Operate efficiently with automation
- Quickly get an integrated view of your AWS or other resources
- Proactively monitor to enhance end user experiences
Native integration for other AWS services such as KMS, IAM, ECS, EC2, DynamoDB, CloudTrail, Lambda, S3, Kinesis, and API Gateway.
- Free plan available
- Pricing upon request
- Rating: 5/5
Pros & Cons of Amazon CloudWatch
Pros | Cons |
Integrates natively with other powerful AWS tools | Expensive |
Strong logging features | Relies heavily on AWS |
Collects metrics from several AWS sources |
|
Top 4 Cybersecurity Trends for 2024 & Beyond
#1 - The Rise of Quantum Computing
One of the most prevalent cybersecurity trends for 2024 & beyond is quantum computing.
The rise of quantum computing presents both solutions and threats to cybersecurity. On the other hand, it can increase encryption methods and build more sophisticated algorithms to identify cyber-attacks.
It includes enhancing existing encryption techniques and preparing systems to be resilient against the advanced capabilities of quantum technologies.
#2 - Zero Trust Cybersecurity
The adoption of zero-trust cybersecurity will continue to grow. This model emphasizes the principle of "never trust, always verify" for all users, devices, and applications within a network. It provides protection against insider threats, external breaches, and lateral movement within the network.
Implementing a zero-trust framework can strengthen your business's security posture and reduce the risk of unauthorized access.
#3 - Multifactor-Authentication
Another cybersecurity trend for 2024 & beyond is multi-factor authentication for protecting accounts and data. MFA requires users to provide several forms of verifications such as passwords, a smartphone lock and biometrics to provide an extra layer of security.
In 2024, this cybersecurity trend will be a non-negotiable security measure for both individuals and businesses. It significantly minimizes the risk of unauthorized access, making it an essential part of cybersecurity strategy. Expect to see a surge in the adoption of MFA as organizations prioritize safeguarding sensitive and confidential information.
#4 - Regulatory Compliance
Compliance with data protection regulations such as GDPR and CCPA will remain a priority for organizations. It drives investments in cybersecurity measures to ensure compliance and protect sensitive data and the biggest cyber threats.
Overall, the future of cybersecurity will be characterized by the continued evolution of technology, the growing sophistication of cyber threats, and the increasing importance of proactive cybersecurity strategies to protect against emerging risks.
As we've explored the top cybersecurity threats and trends for 2024 and beyond, it's clear that the digital landscape is evolving rapidly, bringing new challenges and necessitating more robust defenses. Secure your business with VLink's cybersecurity software solutions.
Get Cybersecurity Software Solutions for your Business with VLink!
VLink is a leading software development company with many years of experience delivering comprehensive cybersecurity software solutions. Our services include endpoint security, network protection, data encryption, identity management, and security awareness training.
With expert support and proactive monitoring, we ensure your business stays secure in today's digital landscape.
Whether you're concerned about malware, ransomware, or data breaches, VLink has you covered. Protect your assets and data with customized solutions designed to meet your unique needs.
Please don't wait until it's too late! Contact us today and take the first step towards a secure future.
Frequently Asked Questions
Cybersecurity means protecting your device, networks, and data from unauthorized access, cyberattacks, and data breaches. It involves implementing security measures, protocols, and technologies to safeguard digital assets and ensure confidentiality, integrity, and availability of information in the face of evolving cyber threats.
To mitigate insider threats in your organization, implement strict access controls limiting employees' access to sensitive data, conduct regular security training to raise awareness about insider threats, monitor employee behavior and activities for suspicious patterns, and establish protocols for reporting and responding to insider threat incidents promptly and effectively.
To mitigate insider threats in your organization, implement strict access controls limiting employees' access to sensitive data, conduct regular security training to raise awareness about insider threats, monitor employee behavior and activities for suspicious patterns, and establish protocols for reporting and responding to insider threat incidents promptly and effectively.
Future cybersecurity threats include:
- AI-powered attacks.
- Sophisticated ransomware.
- IoT vulnerabilities.
- Supply chain compromises.
- 5 G security challenges.
- Biometric data breaches.
- Deepfakes for social engineering.
- Quantum computing risks.
Mitigation requires advanced defenses, ongoing vigilance, and collaboration across sectors.








