The advantages of cloud computing are understood by businesses across all industries. While some are just getting started with their migration as part of digital transformation initiatives, others are implementing sophisticated multi-cloud, hybrid strategies. Data security in cloud computing is one of the major obstacles at any level of deployment because of the distinctive hazards that technology entails.
Data must be safeguarded against unauthorized access since it is the most important business asset for businesses and their clients. Insightful data analytics combined with always accessible and protected data promotes company innovation, boosts customer happiness and loyalty, and, most importantly, provides a competitive edge in the market.
The conventional network perimeter that guided cybersecurity efforts in the past is compromised by the cloud. A distinct strategy is needed for data security in cloud computing, one that considers both the complexity of the data governance and security structures there as well as the dangers.
What is Data Protection in the Cloud?
Any business using the cloud for information archival or active access must prioritize cloud data protection. These precautions guarantee that only authorized workers may access sensitive data and safeguard it from hackers, mistakes, and breaches.  The CIA triad—data availability, confidentiality, and integrity—are the fundamental tenets of information security and data governance—also apply to the cloud:
The CIA triad—data availability, confidentiality, and integrity—are the fundamental tenets of information security and data governance—also apply to the cloud:
- Confidentiality: Protecting data from illegal access and disclosure is known as confidentiality.
- Integrity: restricting alterations that are not authorized and making data trustworthy.
- Availability: Making sure the data is completely accessible and available when it's needed.
Both businesses that are internally managed and businesses that are managed by a third-party service provider are subject to cloud data security.
As businesses acquire, use, and store larger amounts of information crucial to their processes, especially when utilizing SaaS apps and online portals, it is more important than ever to pay attention to data protection within the cloud managed services.
To learn more about the advantages of cloud data protection, best practices for cloud data protection, and other topics, keep reading.
Common cloud data security risks
The cloud presents a number of hazards when it comes to data that the company must handle as part of its security plan. As businesses increasingly acquire, store, and analyze vital data on the cloud, cyberattacks and data breaches pose the highest hazards.
A few of the typical threats businesses face because of the cloud include:
- Regulatory noncompliance—There is always a sense of complexity while achieving requirements for the General Protection Data Regulation (GDPR) or the Healthcare Insurance Portability and Accountability Act (HIPAA).
- Data loss and data leaks— Data loss and data leaks can be caused by inadequate security procedures, such as incorrect cloud system setups, or threats from insiders.
- Loss of customer trust and brand reputation— Customers rely on businesses to protect their personally identifiable information (PII), thus when a security event results in data compromise, businesses suffer a loss of client goodwill.
- Business interruption— One of the top five worries among risk experts worldwide regarding cyber vulnerability is company disruption, namely that caused by supply chains or cloud platforms failing.
- Financial losses— the price tag for data breaches, incident response, business interruption, and other cloud security event-related expenditures can reach hundreds of millions of dollars.
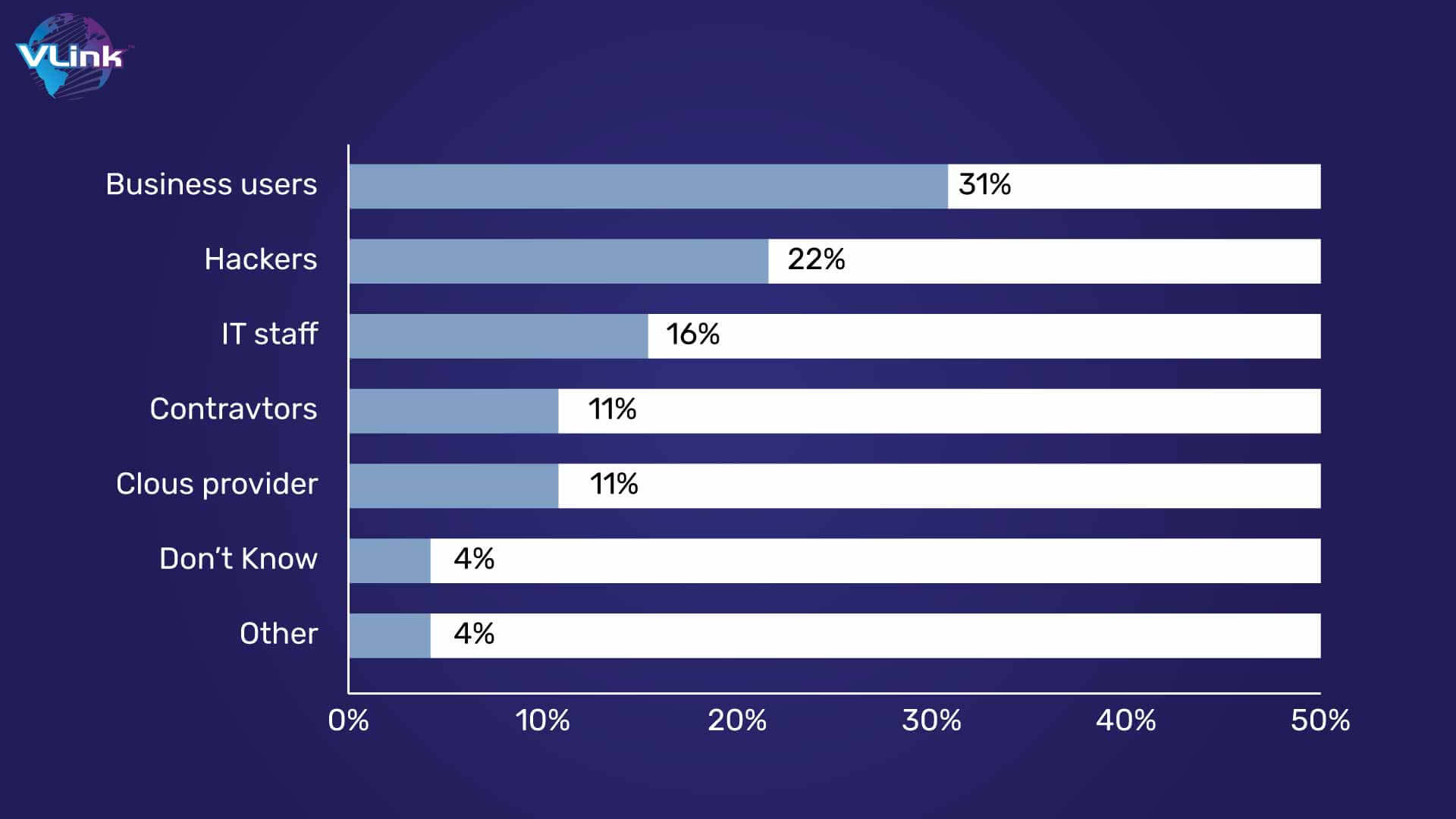
According to a SailPoint report, for instance, 25% of businesses with IaaS implementations have seen data breaches and 45% have faced cyberattacks.
You can see that business users face major threats in cloud security
 According to further study, the growth of cloud services is currently the second-biggest obstacle standing in the way of IT security experts' capacity to respond to a data breach.
According to further study, the growth of cloud services is currently the second-biggest obstacle standing in the way of IT security experts' capacity to respond to a data breach.
Cloud Data Protection Best Practices
When storing data and utilizing critical services in the cloud, there are a number of recommended practices to follow. By including these procedures in business protocol, it is ensured that data is kept secure and secured and that illegal access and other possible breaches are prevented.
- Backup Data
Regular data backups and replications kept in several places are effective ways to make sure you don't lose important information. It is simple to automate this procedure so that it runs on a set schedule at regular intervals.
Data in the cloud is safeguarded by regular backups, which are vital to avoiding significant issues in the case of component failures or system malfunctions.
- Evaluate Built-In Security
Data must always be protected by a security provider, who must also have the necessary tools, internal procedures, and control features. Additionally, they must be open and honest with their clients about their compliance requirements.
In order to satisfy the requirements of regulatory compliance and offer the organization transparent services, these suppliers should be certified.
- Use File-Level Encryption
Users of cloud services should think of file-based encryption as an additional layer of security or as the cornerstone of cloud security. By manufacturing data shards to be kept in several places, this method enables data fragmentation, which lowers fees and prevents system intrusions.
- Enable cloud workload protection.
Containers, Kubernetes, and serverless services are just a few of the workloads that are covered by cloud workload protection (CWP), which enables businesses to create, manage, and secure cloud applications from development to production.
- Strong Credential Policies
Ensuring that only particular people have strict access is another way to improve security. Data leaks and assaults are avoided by using strong credentials. Using complicated passwords, giving access to people you trust, and only giving people access that is required for their jobs are a few strategies.
- Securely Transfer Data
Using SSL and encryption for all communication operations is one way to communicate data safely in the cloud. Then, you can monitor the data and see who has access to it.
 Users can also limit access at any time, see when it has been transferred to other people or organizations, or see when it has been cancelled. These procedures aid businesses in abiding with legal requirements.
Users can also limit access at any time, see when it has been transferred to other people or organizations, or see when it has been cancelled. These procedures aid businesses in abiding with legal requirements.
- Secure Devices
Endpoints are one of the most significant components in cloud security setup. Leaks and attacks are incredibly dangerous to these user endpoints. A significant risk to the security of a business can be attributed to employee mobile devices that can access cloud services.
It would also be necessary to ensure that security endpoints are equipped with additional measures and protocols, as well as the possibility of limiting data transfers between cloud services.
These best practices have been used by the biggest third-party security providers, with a view to protecting your information and fending off hackers.
Why should businesses store data in the cloud?
Cloud computing has become a preferred choice for organizations, owing to its crucial role in almost every digital transformation strategy. Enterprise organizations can, in particular, benefit from the use of cloud data storage and this is as follows:
- Lower costs
Due to more efficient features, time-saving operations, and increased productivity, cloud storage becomes more cost-effective for businesses.
- Resource optimization
Usually, the customer service provider is responsible for maintaining cloud infrastructures such as servers, hardware, databases or infrastructure elements within a cloud model.
Moreover, there is no longer a need for organizations to host or maintain on-premises components. It also allows staff to be redeployed to other areas, such as customer support or business modernization, not only reducing overall IT costs.
- Improved access
With no Internet connection required in order to enable a modern digital workforce, any authorized user can access the cloud hosted database through virtually all devices and locations around the world. 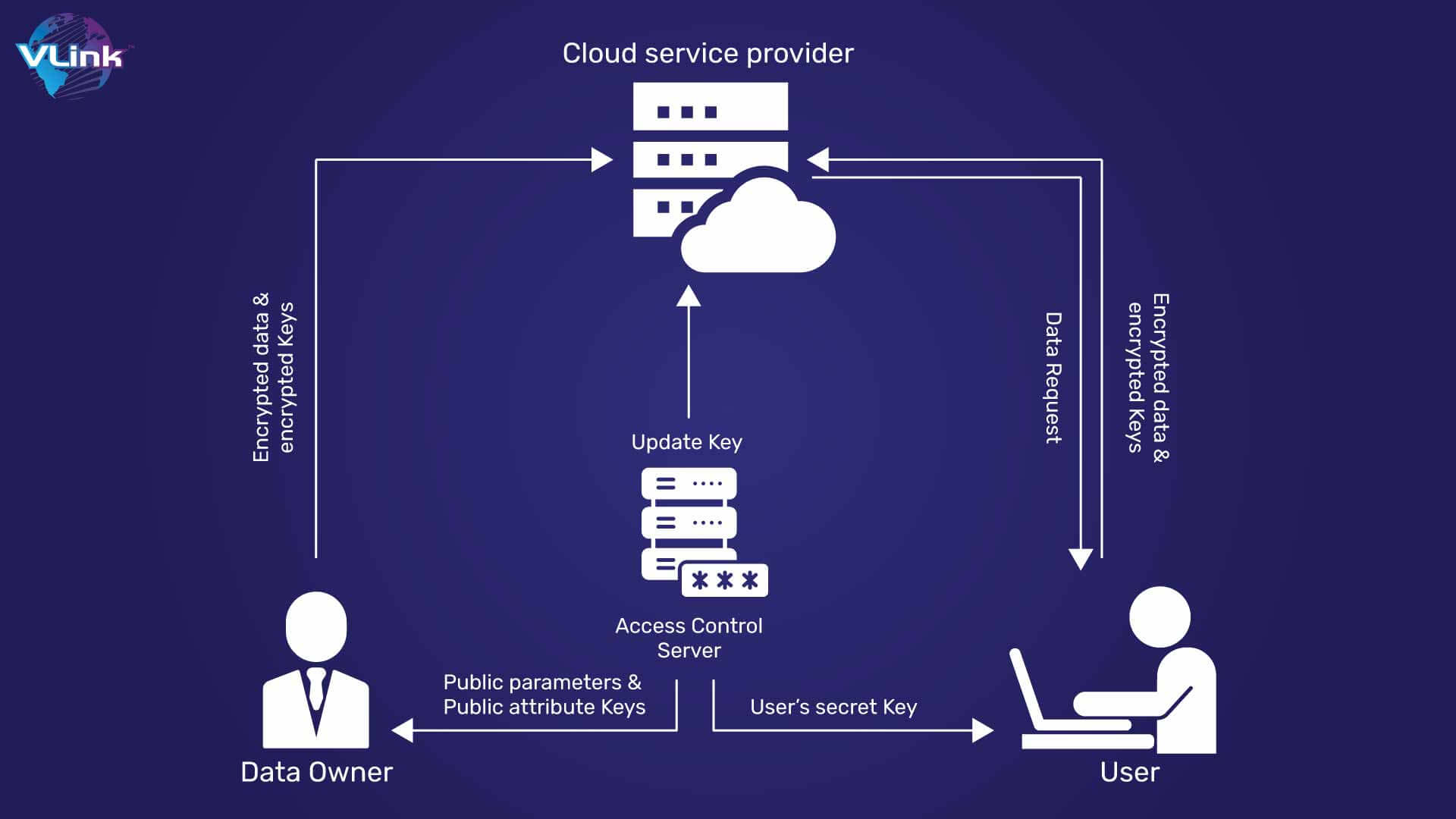
- Scalability
There is flexibility in cloud resources such as databases, enabling them to be rapidly spun up or down according to the business's specific needs. This enables a better, timelier and cost-effective way for an organization to cope with surges in demand or seasonal fluctuations.
As long as the organization is adopting a holistic, strong cybersecurity strategy dedicated to protecting it from risks and threats in an environment where cloud services operate, they will not be more secure than physical servers or data centers.
VLink assures top-notch security with cloud app development
Companies that are operating in the cloud have a number of considerations, whether or not they're dealing with a Hybrid or fully cloud owned environment. Companies need highly skilled and qualified cloud security providers with the latest tools and techniques to ensure that their data is safe, as threats are everywhere at all stages of its creation, transfer, or storage.
By offering solutions that match your organization's individual needs, a security cloud development company such as VLink can help. In addition to the services offered by Veritas to clients to ensure security, measures to protect data overload and access are part of these services.
The primary objective of VLink when servicing clients is to protect data in the cloud so as to ensure that they are kept safe and remain secure, whilst monitoring their systems at all times. We're one of the most prominent cloud security providers on earth, capable of helping with everything from disaster recovery to data protection in the cloud.
Frequently Asked Questions
Data security is the use of cloud computing to protect data, and further digital information assets from risks such as cyber insecurity, human error or insider threats. It's driven by technology, policies and processes to ensure that your data is not disclosed or available for those who need it in cloud computing environments.
Due to the fact that most organizations already use cloud services in one form or another, it's critical for their security. The protection of data and business content, e.g., customer orders, secret designs for documents or financial records, is a vital element in Cloud Security.
Cloud security is a much wider area than cyber security, and every variety of attacks cannot be prevented. But the risk of cyber-attacks is greatly reduced by a well-planned strategy for cloud security. Cloud computing, unlike on premises servers, is usually more secure in the face of these risks.







