The Health Insurance Portability and Accountability Act (HIPAA), which was passed in 1996, established guidelines for protecting all patients' private, sensitive information. According to the law, health insurance companies must uphold stringent privacy and security regulations that are all intended to safeguard patients' personal information and all electronically protected health information, or ePHI.
Since then, the U.S. Department of Health & Human Services' enforcement of these regulations has completely changed how healthcare institutions manage and safeguard patient information. Successful healthcare firms that adhere to HIPAA regulations use stringent internal procedures and invest a lot of effort in making sure the healthcare software system is reliable.
That places a lot of burden on testing healthcare software, especially for QA and software testing experts that may not be completely familiar with all HIPAA compliance rules. Teams may experience anxiety, confusion, and frustration from one software development cycle to the next when there may be serious repercussions for the entire company if your program is not fully tested.
But before we move to knowing the significance and practices to build HIPAA compliant software, let’s understand the concepts.
What is HIPAA?
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a federal law that imposes requirements for safeguarding sensitive patient health information to prevent its unauthorized disclosure without the patient's awareness or consent.
In order to implement the provisions of HIPAA effectively, the U.S. Department of Health and Human Services (HHS) introduced the HIPAA Privacy Rule. This rule outlines the standards and regulations pertaining to the privacy of patient health data. Additionally, a subset of the information covered by the Privacy Rule is subject to protection under the HIPAA Security Rule. 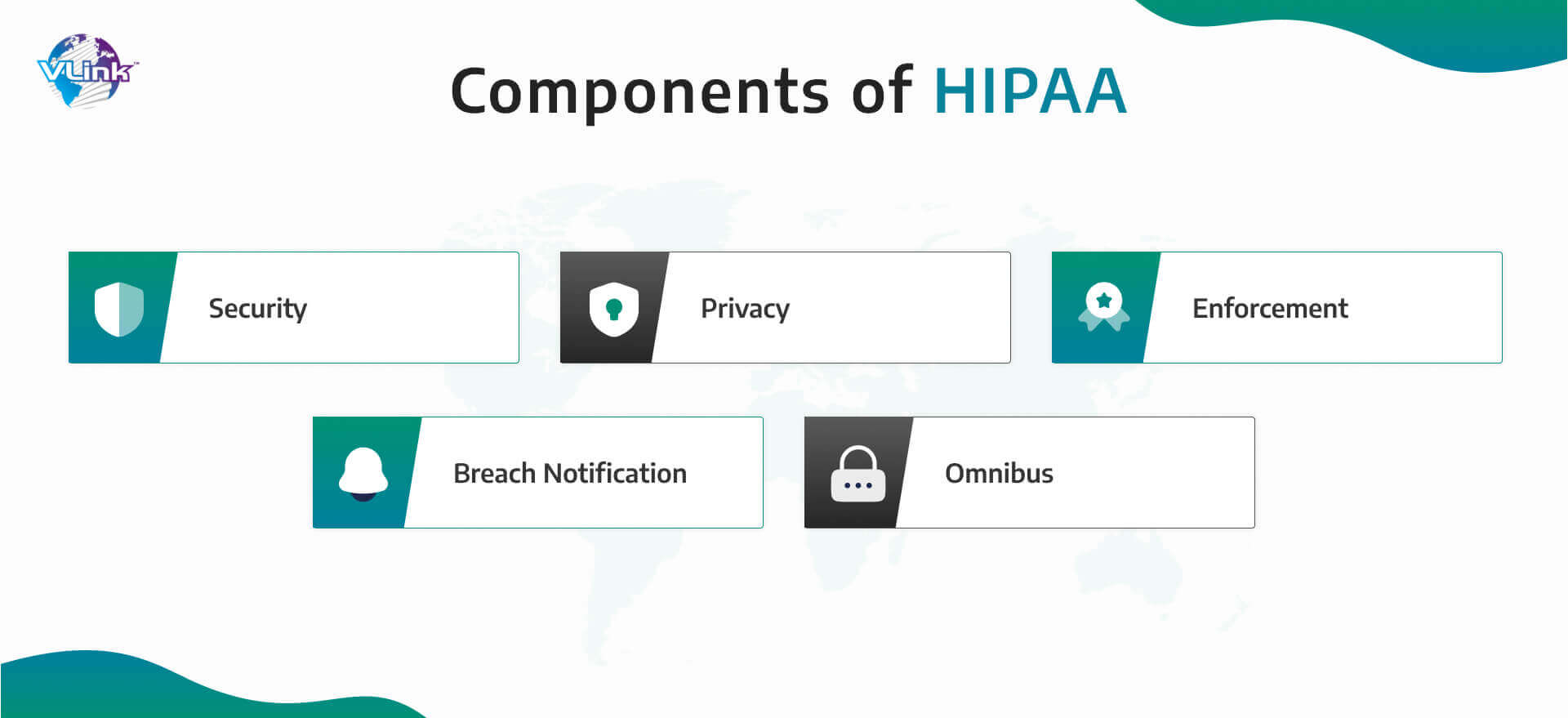 The benchmark for protecting sensitive patient data is set by the Health Insurance Portability and Accountability Act (HIPAA). HIPAA's main goal is to safeguard people's rights to know and be in control of how their personal data is utilized while it is being gathered by various organizations.
The benchmark for protecting sensitive patient data is set by the Health Insurance Portability and Accountability Act (HIPAA). HIPAA's main goal is to safeguard people's rights to know and be in control of how their personal data is utilized while it is being gathered by various organizations.
The Privacy Rule focuses on utilizing significant information for the sake of preserving the privacy of those who require medical treatment and care.
Let’s understand what Is included under HIPAA compliance when it comes to software testing for quality and performance purposes.
Considerations in HIPAA compliance
There are five sections that are included in HIPAA compliance, and each one focuses on a distinct area of managing and protecting sensitive patient data. While implementing software testing best practices for HIPAA compliance, you should be aware of these crucial factors:
1. Security
There are three types of safeguards included under the security part of HIPAA requirements: technological, physical, and administrative.
These are some of the technical precautions covered under HIPAA:
- In the event of an emergency, a plan must be in place for safely disclosing patient data.
- When data exits the internal firewall, it must be encrypted.
- Every time a person accesses patient data, they must frequently log out of their devices.
- When data has been altered by a third party, there should be a technological way to detect it.
Let’s take a look at the physical security guidelines highlighted by HIPAA:
- A list of sites where sensitive data can be viewed must be kept up to date often.
- Each hardware component handling healthcare data has to be identified.
- If a worker has access to the data via a mobile device, it must be deleted once the worker departs the company.
- Users who have access to data should be subject to a set of clearly defined policies.
The following are the considerations for administrative protection:
- Policies for risk assessment and management ought to be in place.
- A business associate agreement must be executed if any other parties have access to the data.
- The organization must have a security and privacy officer.
- A backup strategy outlining the company's security measures is required.
2. Privacy
Before using a customer's data for marketing or research, you must get their permission. An NPP (Notice of Privacy Policy) is required while implementing custom software services for healthcare, as well as a backup policy in the event that the NPP is broken.
Your privacy policies must be made public and clearly stated. You must be able to respond to a customer's request for a copy of their record within 30 days.
3. Enforcement
Access and authentication methods must be in place. PHI (Protected Health Information) must be protected using encryption. Any outside tech partner that assists with the development or testing of your product must be HIPAA compliant. Regular security risk assessments are required.
4. Breach notification
It should be simple for the accountable parties to see a violation. A data breach must be handled according to an established process. In the event of a breach, users, partners, and authorities must be notified. The media should also be informed if the breach affects more than 5,000 patients.
5. Omnibus
All workers should have access to a HIPAA Privacy and Security Awareness Training Program. If the patient asks for an electronic copy of their record, you must give it to them. The compliance strategy for breach notification should be updated often. The new regulations must always be followed with regard to your ePHI.
Importance of building a HIPAA compliant software
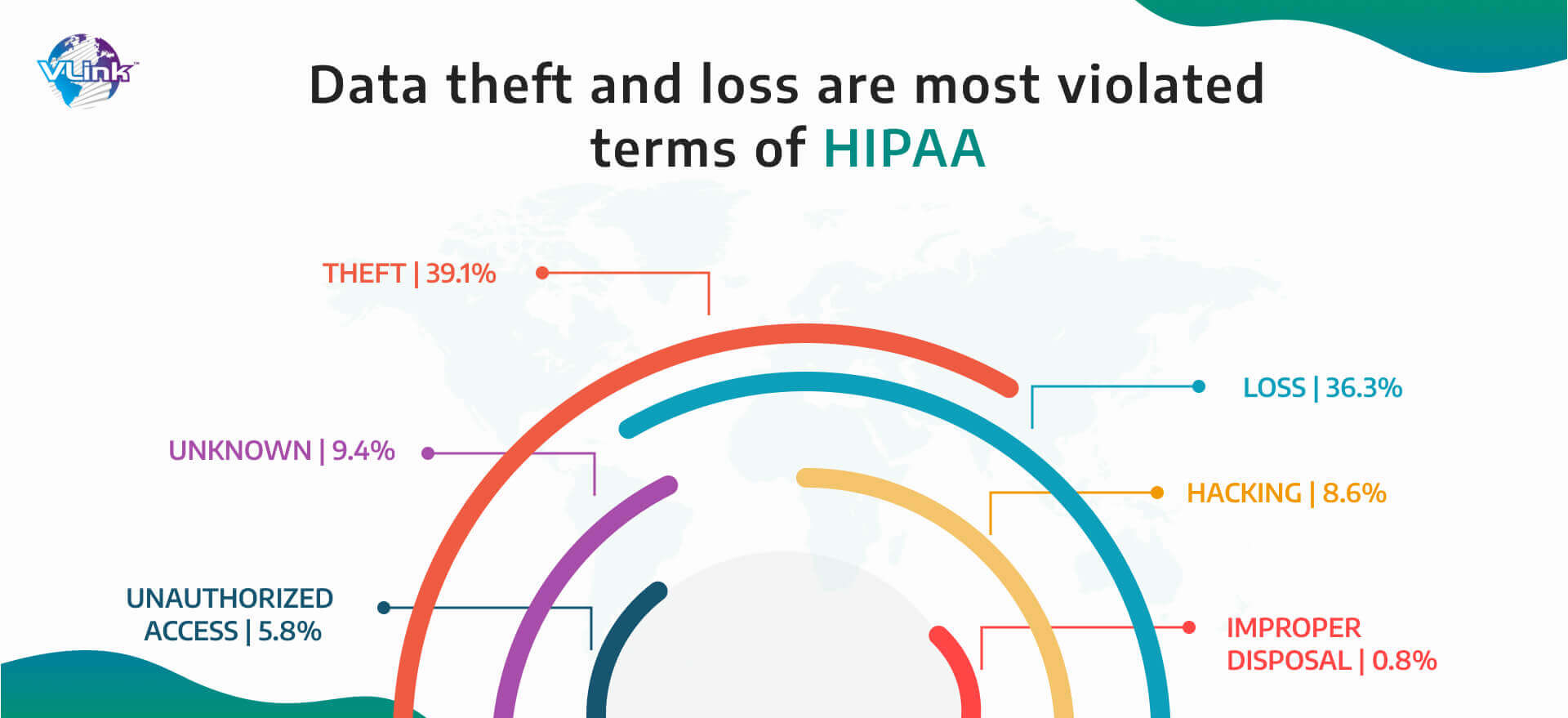
Although security is always a top priority for healthcare service providers to maintain HIPAA compliance, due to the industry's complexity, some issues occasionally go unresolved. Here is what normally occurs when a HIPAA compliance software checklist is missing.
- A lot of data to protect
The designers must have a thorough grasp of what sensitive information is before creating a structure for data security. Evaluating this can be challenging in the healthcare system since the data are kept in several locations including physical storage facilities, EHR systems, data centers, mobile devices, suppliers' offices, etc. in various formats.
- Lack of resources around HIPAA compliance
It is necessary to have attorneys, system architects, cybersecurity specialists, and medical professionals on the team when creating completely HIPAA compliant software. They all give substantial knowledge and time to the project, which is sometimes not achievable due to fixed costs and timelines associated with developing healthcare apps.
- Multiple data access platforms
A uniform security mechanism must be used to secure every platform inside the healthcare system. The infrastructure of a hospital, however, comprises of physical and digital user endpoints, data centers, servers, cloud resources, etc. Investigating MDM development for protecting sensitive data is important to create a unified security infrastructure.
- Lowered flexibility
Multiple security needs can result in a software application that will be inflexible in nature. To manage the experiences of both patients and doctors, healthcare institutions must be adaptable. This puts developers in a position where they must balance flexibility and HIPAA compliance without sacrificing the healthcare experience.
- Need to reassess HIPAA implementation
The application's deployment is only the beginning of the HIPAA compliance testing process. To guarantee your software stays compliant, you will need to undertake routine audits and document updates since a number of factors, including cybersecurity risks, HIPAA rules, and the IT requirements of the healthcare business, are continuously changing.
How to Comply with HIPAA in Software Testing?
Healthcare software testing according to HIPAA rules has become a crucial part in modern era development. Here are some important practices you should follow:
1. Controlling accessibility
A user should only be permitted access to the bare minimum of data required to carry out a specific operation in accordance with HIPAA compliance regulations. These seven methods can be used to implement strict access control:
- A collection of access controls that restricts user access to just particular programs, modules, or sections.
- A special name or number that may be used to monitor and identify each user's identity within the system.
- User-based access that comes with two-factor authentication method to access information.
- Role-based access that comes with different roles executing different purposes according to the software needs.
- Context-based access that is limited to particular dates, times, or gadgets on a particular network or information system.
- Efficient procedures are established to react under emergency and obtain ePHI.
- Automated processes come into action to logout sessions after a particular period of time of if there is an inactivity.
- ePHI will go under encryption & decryption.
2. Encrypting data before sharing
All information that users communicate should be completely secured, with only authorized users being able to decode it. The same holds true for information kept elsewhere, such as on the cloud.
When sending encrypted data, adhere to the following best practices to comply with HIPAA regulations:
- To stop unauthorized parties from accessing system data, use secure encryption keys.
- Data encryption should be prioritized, irrespective of its location or storage sources.
- Analyze the effectiveness of algorithms at encrypting data often.
After testing, you should do a risk analysis to discover any data loss during transfer or attempted unauthorized access.
3. Data sanitization
When conducting application testing within a healthcare organization, the risk of data leakage is a constant concern. To mitigate this risk, it's essential to establish a standard practice of creating test data that simulates real data behavior. 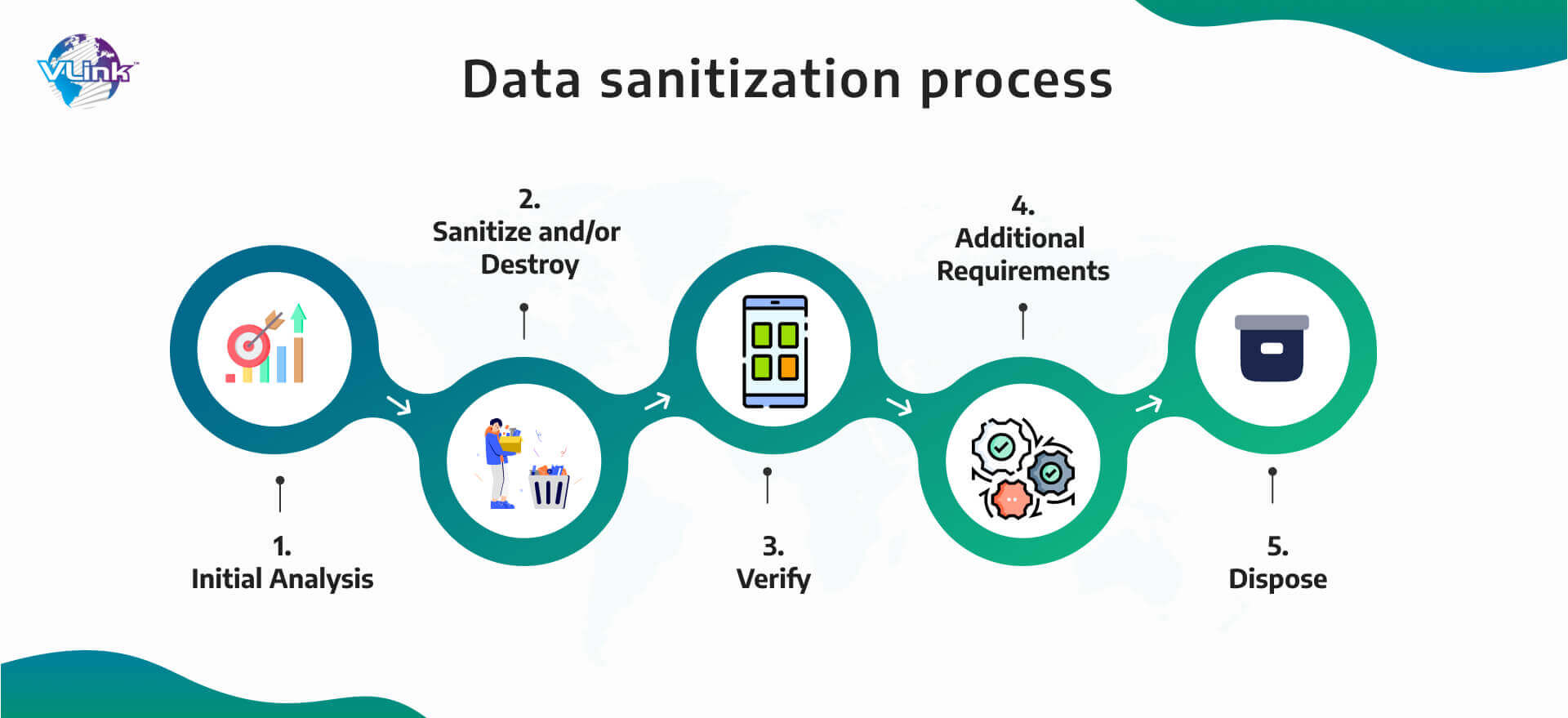 For instance, you can anonymize or conceal existing field data, such as names, addresses, Social Security numbers, phone numbers, and more, by replacing them with generic data.
For instance, you can anonymize or conceal existing field data, such as names, addresses, Social Security numbers, phone numbers, and more, by replacing them with generic data.
To ensure the highest level of security and efficiency, the recommended approach is to employ automated test data generation tools explicitly designed to handle large datasets while maintaining high performance.
4. Structuring data sets
It’s necessary to standardize the information tested before it will be analyzed for the verification and validation of modules within the application. Structuring the data will simplify examining, processing, and executing the information at different stages of testing.
5. Auditing the processes
Implement an audit trail to keep track of all patient data-related acts in order to comply with HIPAA compliance regulations. This covers additions, removals, revisions, and pretty much every other action you can think of.
The audit trail also records the user who did the activity and the time it happened. The audit trail may be used to cross-reference any suspicious activity or data breach to establish its origin.
6. Implement load balancing
Since the loss of patient data might endanger life, this is arguably the most important justification for adhering to HIPAA regulations. To ensure that the system can continue running normally while backups are being made, failover planning and load balancing are implemented. 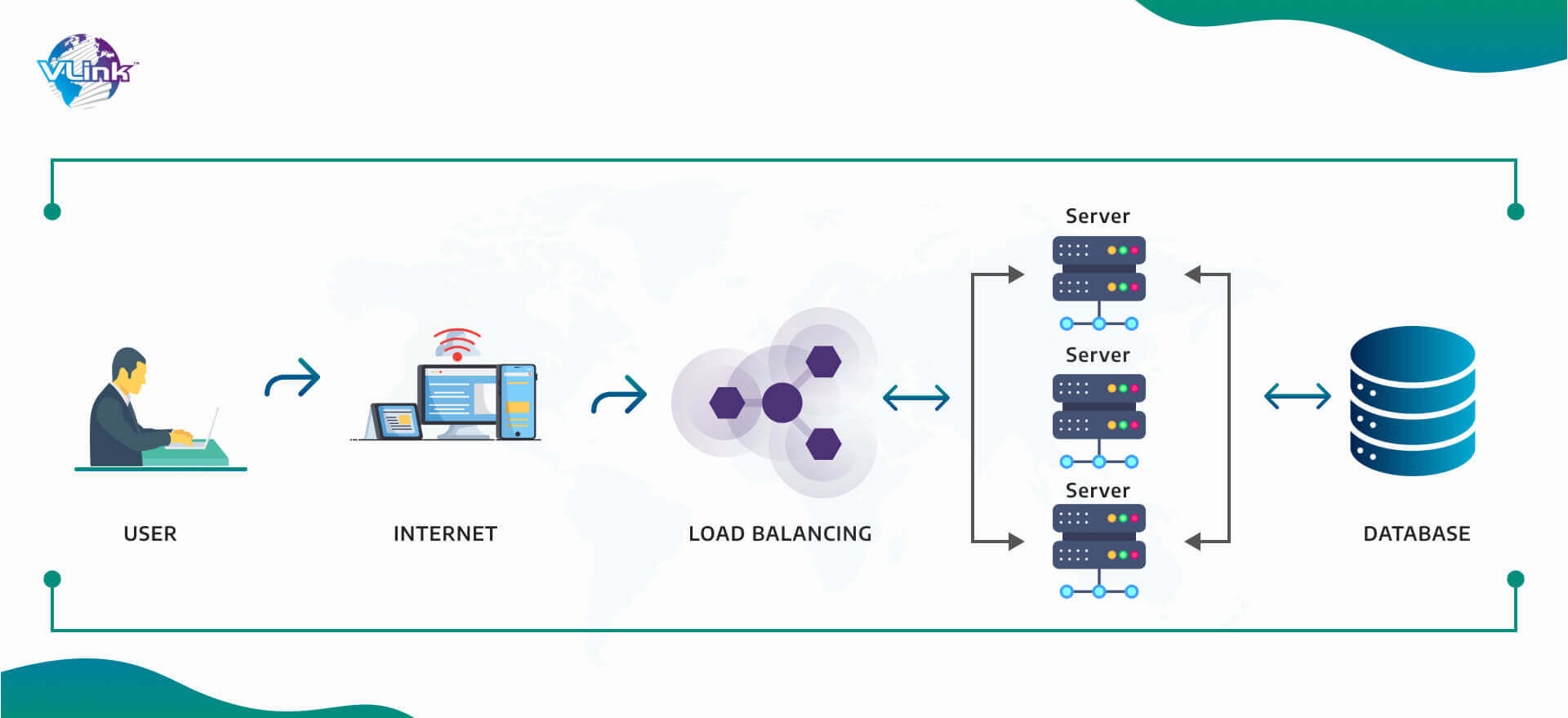 It also establishes if a system can provide more resources when necessary and whether it can identify that requirement once it occurs. When properly built and fully tested, a solid failover plan should offer almost total data protection, little data loss, and quick recovery in the case of an incident.
It also establishes if a system can provide more resources when necessary and whether it can identify that requirement once it occurs. When properly built and fully tested, a solid failover plan should offer almost total data protection, little data loss, and quick recovery in the case of an incident.
How VLink can help in building HIPAA compliant software
With the help of these five HIPAA software testing best practices and the method we use for HIPAA compliance testing; we can design applications that are compliant with regulations and are also breach-proof. We do this by basing our design, development, and maintenance efforts on the HIPAA compliance software checklist.
By spending expenses on compliance verification and assessment services, one may be audit-ready at all times and avoid paying large fines. VLink, a top testing and QA firm, can assist you with this task with the aid of our most qualified specialists who are skilled in managing compliance checks and audit support operations.







