Many enterprises have benefited from the evolution of cloud technology, which has allowed them to gain competitive flexibility and reduce costs. Today, many businesses have migrated their data center to cloud, and a few others are at the halfway mark.
The cloud computing market is estimated to reach about 1.6 trillion USD by 2030 with a compound annual growth rate of 17.43 % between 2022 and 2030, according to Precedence Research. This market outlook for cloud computing also includes a growth of the threat environment to cloud computing which, thus, calls for security provisions on cloud computing.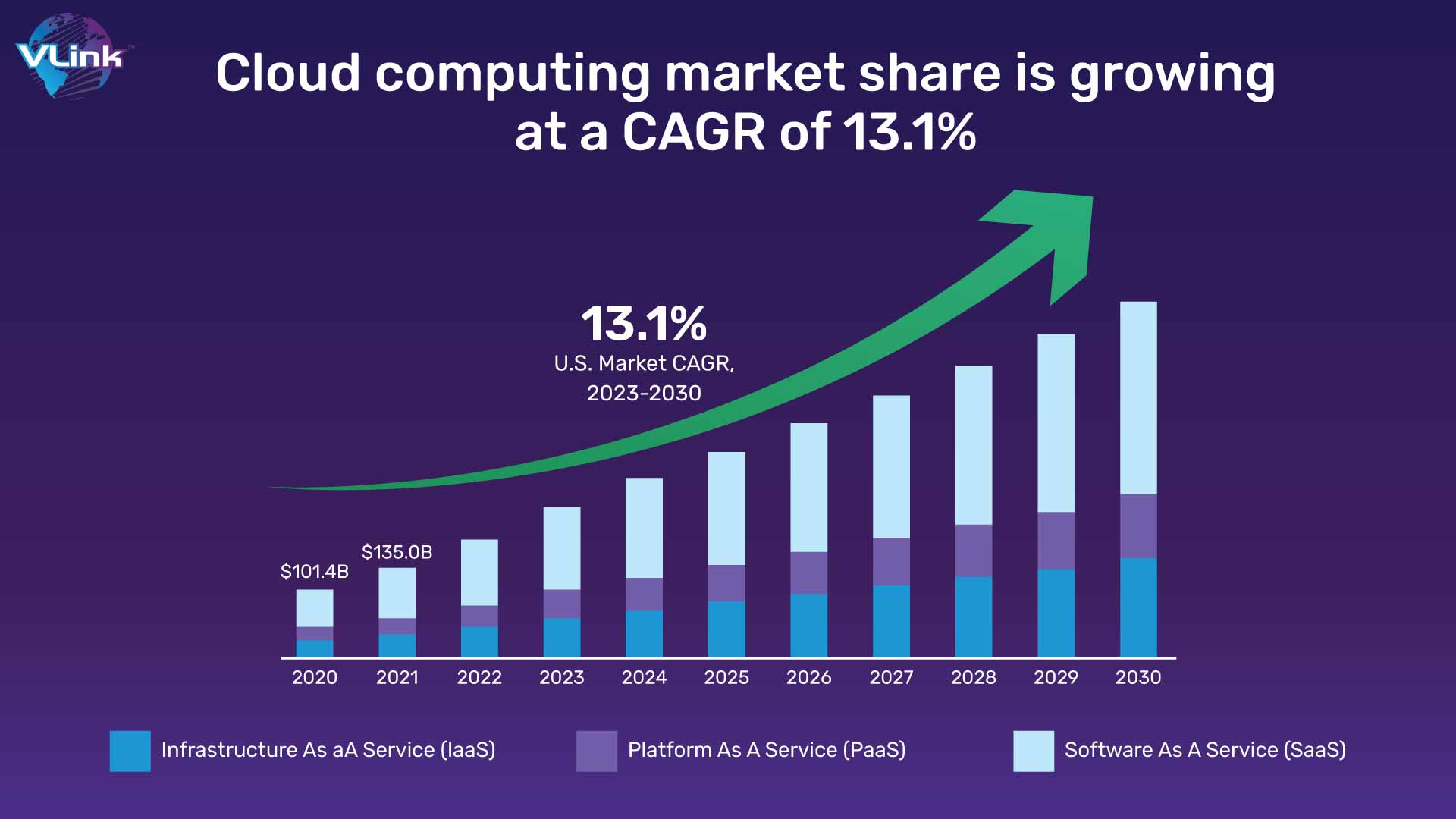 In the past several years, a number of digital transformation trends and dimensions have been adopted to ensure that Cloud's resources are protected from attacks: A TechRepublic report indicates that by 2032 this market will be in excess of $123 billion.
In the past several years, a number of digital transformation trends and dimensions have been adopted to ensure that Cloud's resources are protected from attacks: A TechRepublic report indicates that by 2032 this market will be in excess of $123 billion.
Understanding cloud security concepts
Many business issues such as scalability, cost efficiency and flexibility are solved by cloud computing. It's also about entering a place where it is easy to leave gaps that hackers might exploit for most businesses.
It is also necessary to establish a model of shared responsibility. This means that the cloud service provider oversees securing its own cloud infrastructure, while the customer's responsibility is to protect their data and applications. Although the concept may seem simple, a full approach to cloud security is hard to define.
By 1950, when mainframe computers were being built that could be accessed by a thin and static client, the concept of cloud computing was born. Since then, cloud computing has evolved from static clients to dynamic ones, from software-based systems to service oriented solutions. When businesses were entrusted with data by big companies like Amazon, security problems had begun to emerge. The use of servers to store vital information that customers may not physically access has posed a serious challenge to the traditional notion of security, despite several benefits and efficiency improvements.
When businesses were entrusted with data by big companies like Amazon, security problems had begun to emerge. The use of servers to store vital information that customers may not physically access has posed a serious challenge to the traditional notion of security, despite several benefits and efficiency improvements.
Hosting companies have adopted more elaborate security measures in view of increasing data storage volumes and types.
Top 7 cloud security trends
As more and more organizations have already chosen the technologies that best match their individual platforms, multicloud strategies will soon be a norm rather than an exception. Consequently, it becomes essential to build resilient architecture that is capable of cooperating and functioning with more than one cloud service provider.
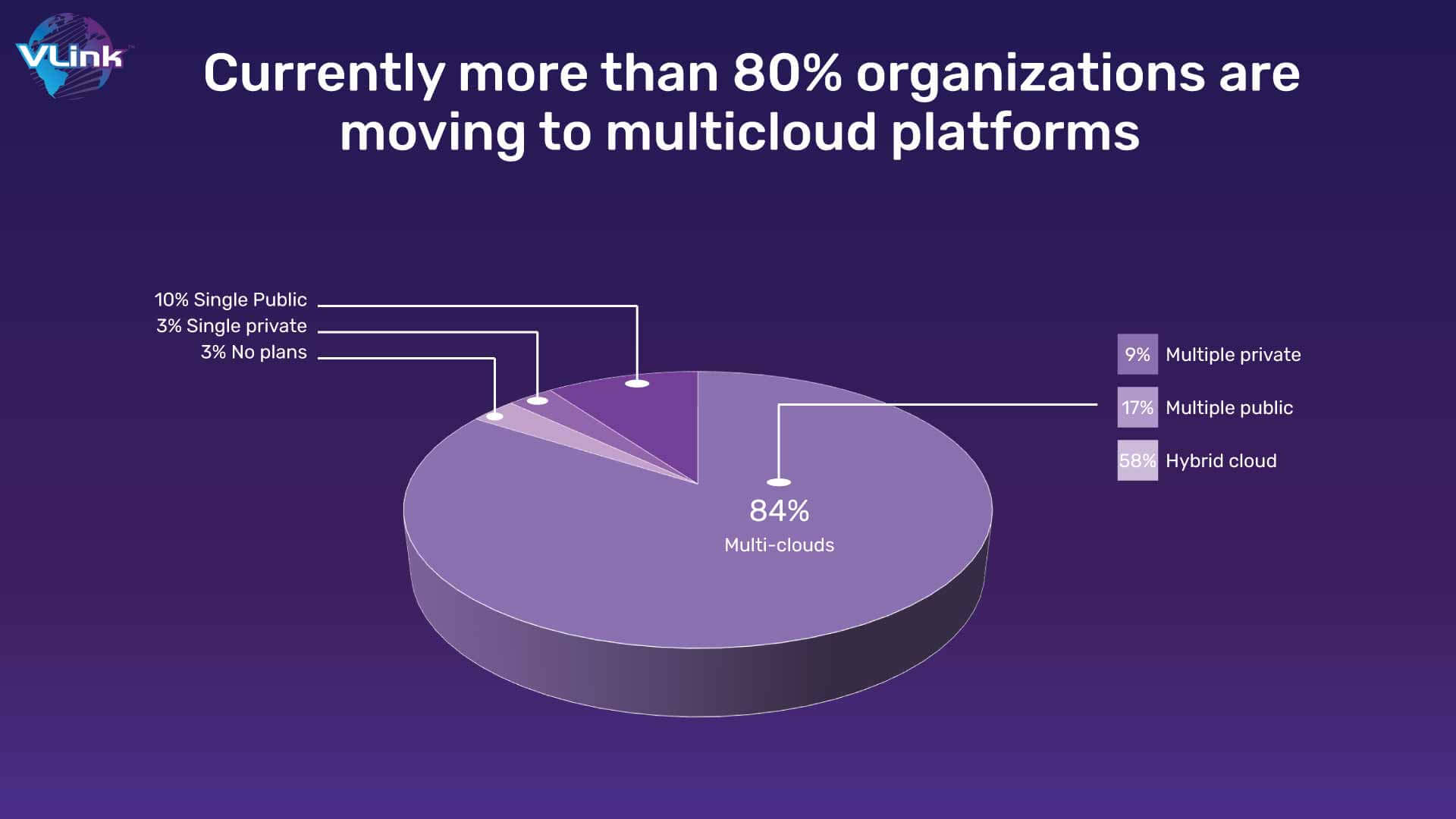 It is definite that the model will be adopted by several organizations together with security practices and tools. This growth area will receive considerable attention by enterprises, which will find new ways to embrace a multicloud strategy to be at the forefront of cloud security.
It is definite that the model will be adopted by several organizations together with security practices and tools. This growth area will receive considerable attention by enterprises, which will find new ways to embrace a multicloud strategy to be at the forefront of cloud security.
To breach the cloud, hackers will seek out weak links in supply chains and intentionally target organizations that have valuable data. This is why cyber security will devise a way to prevent attackers moving laterally by restricting the privileges and entitlements of each private and external identity, such as machine identifications that can access cloud resources.
Successive supply chain attacks have been shown to weaken customer loyalty and trust, which in turn has had a negative public perception of many organizations. Damage to business operations, damage to reputation and financial losses can be mitigated by being prepared.
It is undeniable that the pandemic has stimulated a renewed interest in adopting technology rapidly. Consequently, many organizations have a large number of staff working at home and therefore seek to provide security from the location nearer where they work rather than their headquarters data center.
The Secure Access Service Edge Framework is designed to facilitate rapid adoption of cloud services and ensure that users and devices can access applications, data or services at any time. 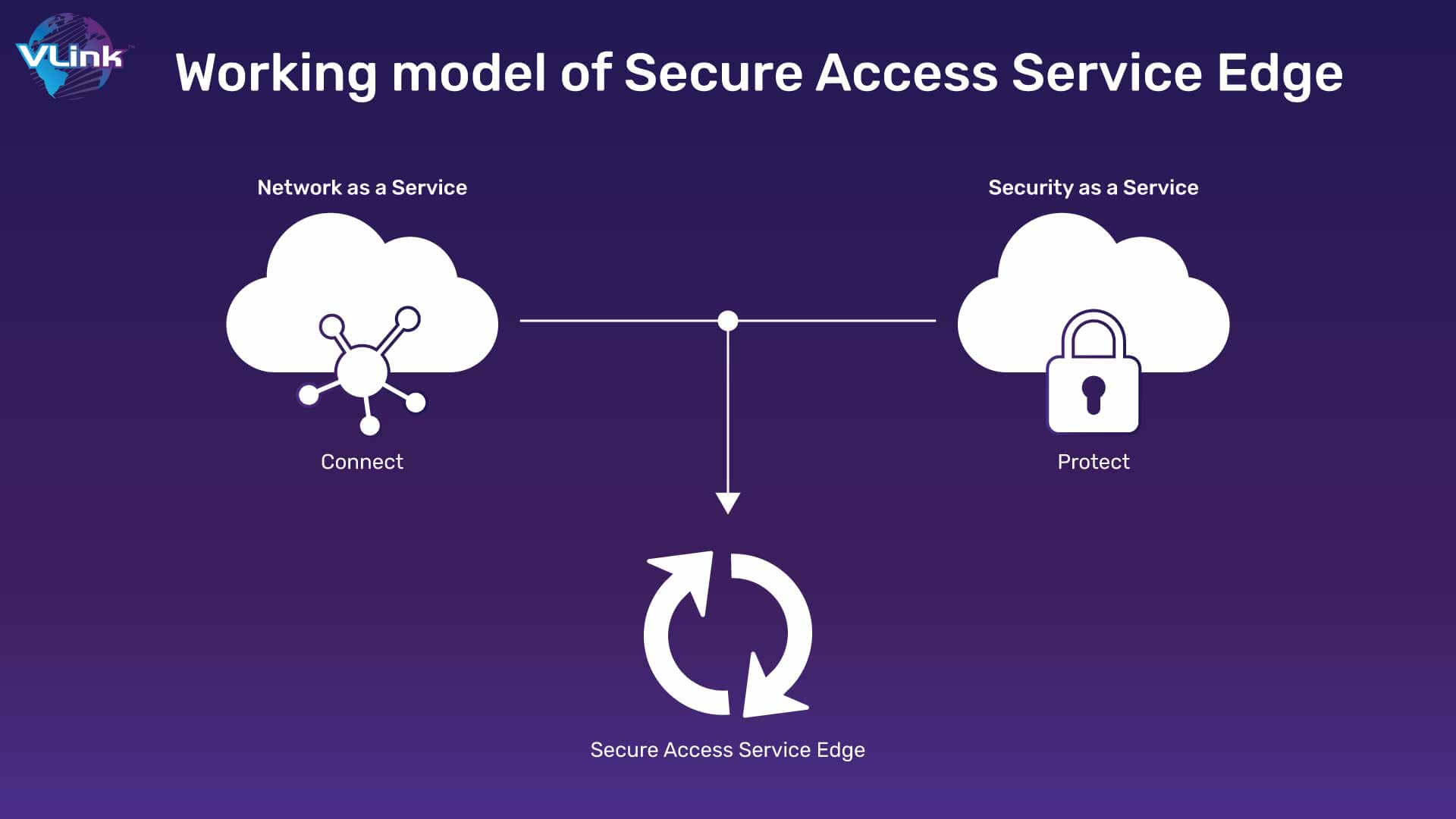 SASE will soon become widely adopted by many organizations, since it is easy to scale a cloud service like SASE as opposed to the VPN gateway.
SASE will soon become widely adopted by many organizations, since it is easy to scale a cloud service like SASE as opposed to the VPN gateway.
The zero-trust approach, which requires all users in the network to be authenticated and authorized, is a vital and practical method of organizational security. This approach will help to shape a security policy that establishes how organizational resources should be arranged and who should have access to information and other cloud services.
This leads to high expectations that more organizations will adopt the Zero Trust security framework in order to defend their cloud resources against attacks.
A significant increase in breaches using the Software as a Service Platform last year cannot be denied. Security products and tools from Software as a Service are growing to combat the recurrence of these malicious attacks. SaaS security posture management tools, for example, are one of the areas where improvements have been made.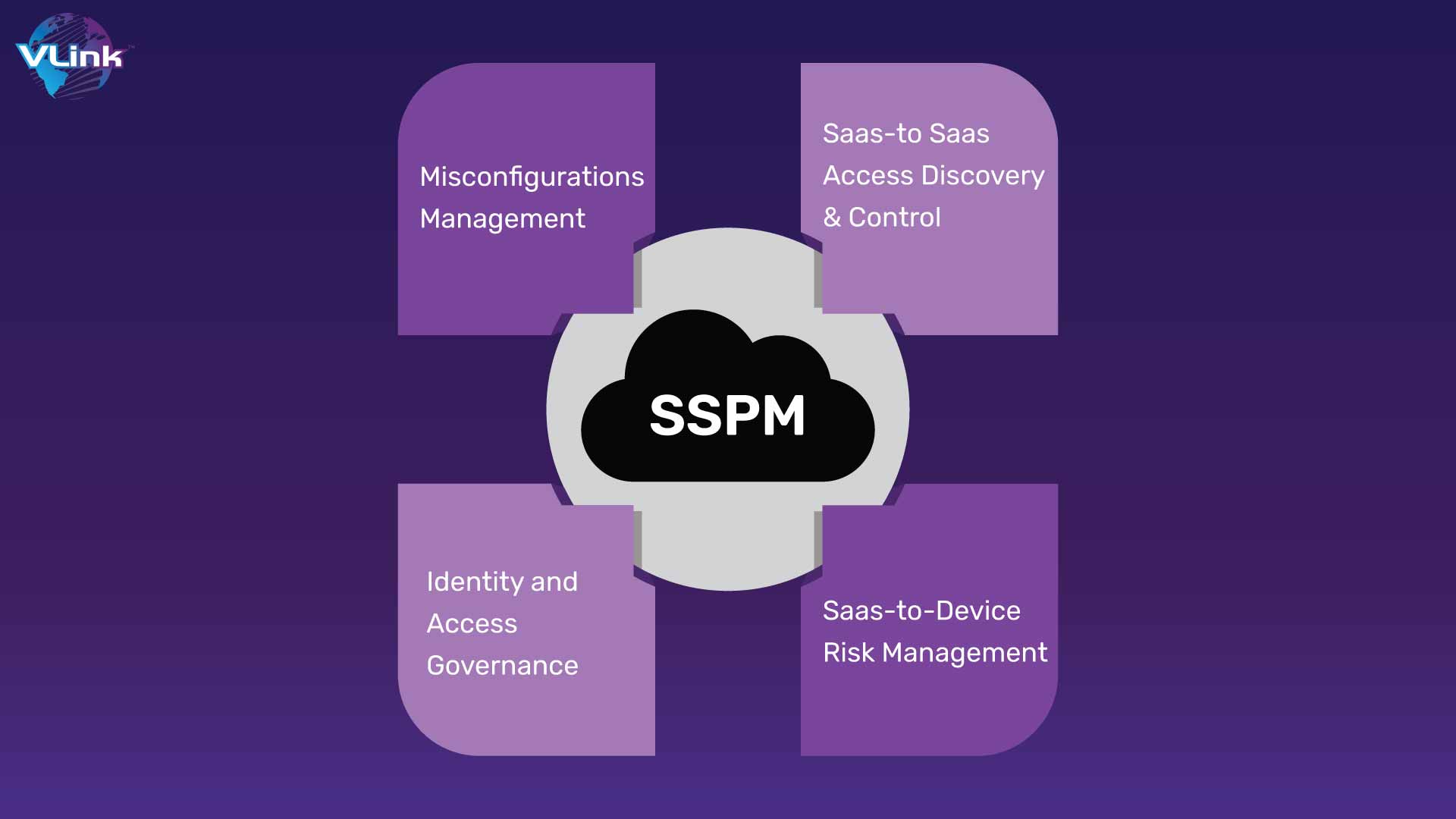 The emergence of SSPM has proven itself to be a game changer in Cloud Security. To ensure that companies are aware of the latest changes or developments in activities while staying within their obligations, you should keep an eye on portfolio`s while choosing a SaaS development company.
The emergence of SSPM has proven itself to be a game changer in Cloud Security. To ensure that companies are aware of the latest changes or developments in activities while staying within their obligations, you should keep an eye on portfolio`s while choosing a SaaS development company.
As a result, there is rapid acceptance of Software as a Service tools among businesses and the number of SaaS platforms supporting these tools will increase significantly.
DevSecOps is a methodology for integrating security protocols throughout the entire Software Development Lifecycle (SDLC). By adopting security measures early in the process, organizations will be able to take proactive action against threats instead of reacting reactively.
In the fast, fully automated development cycle that enables secure innovation, DevSecOps is particularly effective. To implement robust security measures across the supply chain and to make security a continuous process within Continuous Integration/Continuous Delivery pipeline, DevOps and Security teams need to work together.
As a way of supplementing manual security practices, your cloud service is going to be using AI-based Security Software. Businesses will be using AI and machine learning for faster, more accurate detection and response to attacks. The deployment of AI based security solutions is driven by the growth of edge devices and the Internet of Things.
A growing number of businesses are looking to use cloud-based security solutions, relying on biometric identification and machine intelligence in order to protect themselves. As time passes, these technologies will continue to be more cost efficient, effective and productive. Enterprises will increasingly be adopting hybrid architectures which combine automated security with manual processes to reduce the cost and complexity of cloud security solutions. It would also make it possible for them to obtain user data in relation to infrastructure and applications.
Enterprises will increasingly be adopting hybrid architectures which combine automated security with manual processes to reduce the cost and complexity of cloud security solutions. It would also make it possible for them to obtain user data in relation to infrastructure and applications.
Furthermore, the use of technical security practices as well as supervision by human beings would be carried out regarding Cloud environments.
Where does cloud security affect the most?
Businesses open themselves to a wide range of financial and technological risks when they make the use of Cloud technologies but are unaware of their security risk. We'll look at the most dangerous risks that come with cloud adoption and what you can do to reduce them.
1- Cloud Misconfiguration
Some kind of cloud configuration error, which can negatively impact security, is reported by three quarters of all enterprises running on the cloud.
Default passwords, insufficient access restrictions, incorrect authorization controls, insecure data encryption and several other vulnerabilities are some of the main weaknesses.
Due to the proliferation of insider threats and security ignorance, a significant number of these vulnerabilities occur.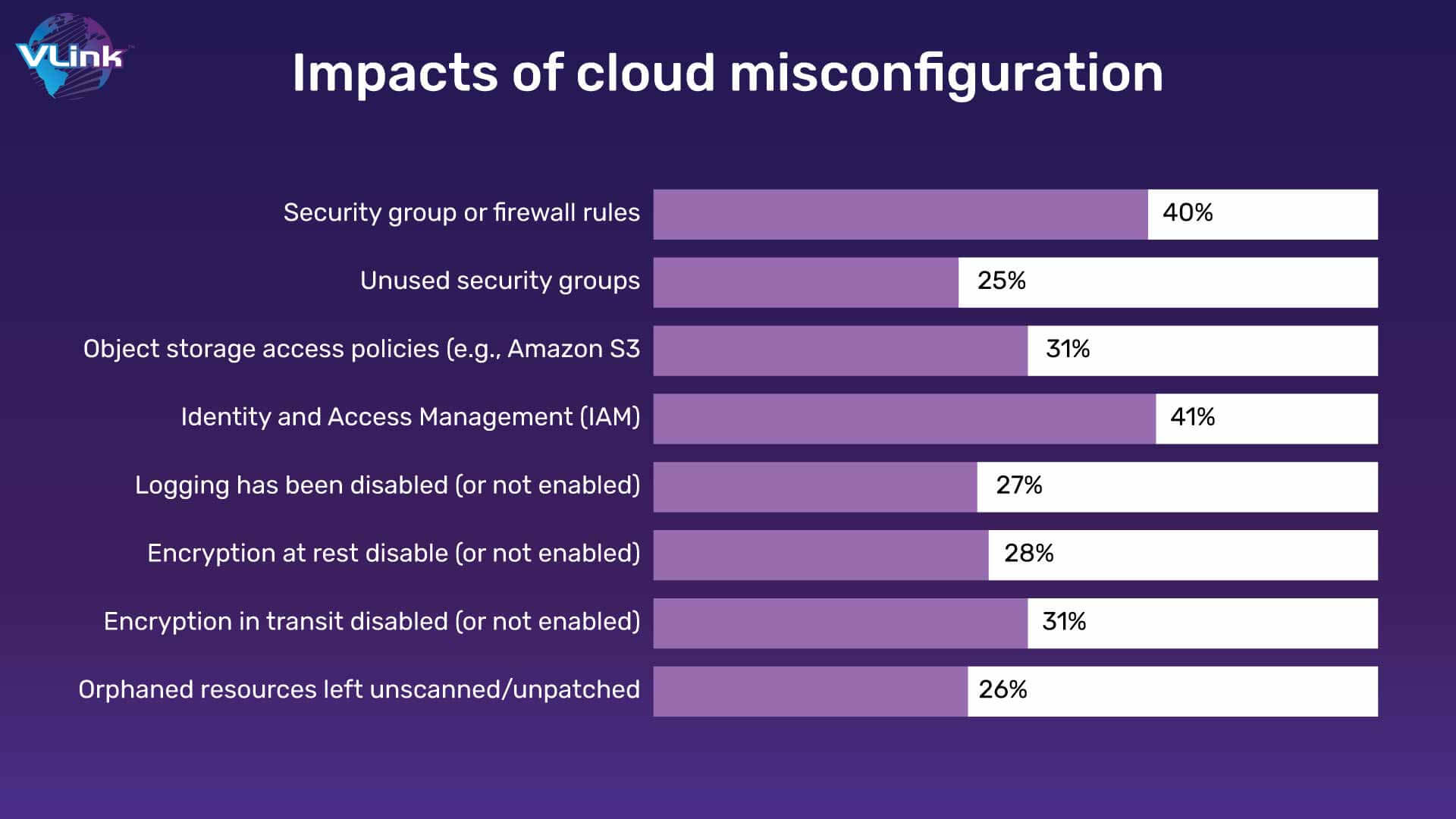 Attempting to customize your cloud usage by setting changes or plugins can also be another way for companies to introduce vulnerabilities. Configuration drift may occur as a consequence of such ad hoc changes, which could lead to availability, management and security problems.
Attempting to customize your cloud usage by setting changes or plugins can also be another way for companies to introduce vulnerabilities. Configuration drift may occur as a consequence of such ad hoc changes, which could lead to availability, management and security problems.
It is good for business to use API, but it's terrible for the security team. Although they are designed to streamline cloud computing processes, APIs aren't always black and white. In a gray area there is the possibility that hackers could take advantage of personal information by leaving APIs unsecure.
One of the main causes for cloud data breaches is a lack of API security. Gartner expects that APIs will be a common vector in cyber-attacks over the period from 2022 onwards.
Security teams believe that malware is not an issue in the cloud infrastructure, particularly when they have implemented endpoint and client-side firewall technology. But malware is now a real threat to cloud services, and you must ensure that the security team has multiple layers of protection when detecting it. When cloud malware gets inside your system, it can spread fast and opens the door to other dangerous threats. Once the malware is activated, it can transfer privileged data to or use keyloggers to obtain access credentials. The damage caused by the malware is going to increase if it's not detected.
When cloud malware gets inside your system, it can spread fast and opens the door to other dangerous threats. Once the malware is activated, it can transfer privileged data to or use keyloggers to obtain access credentials. The damage caused by the malware is going to increase if it's not detected.
The loss of personal and sensitive information and data, both accidentally and intentionally, is the biggest and most important cloud computing threat to organizations today. As more companies allow their employees to use personal devices on the job without putting in place a robust security framework, there will be an increased risk of data breaches.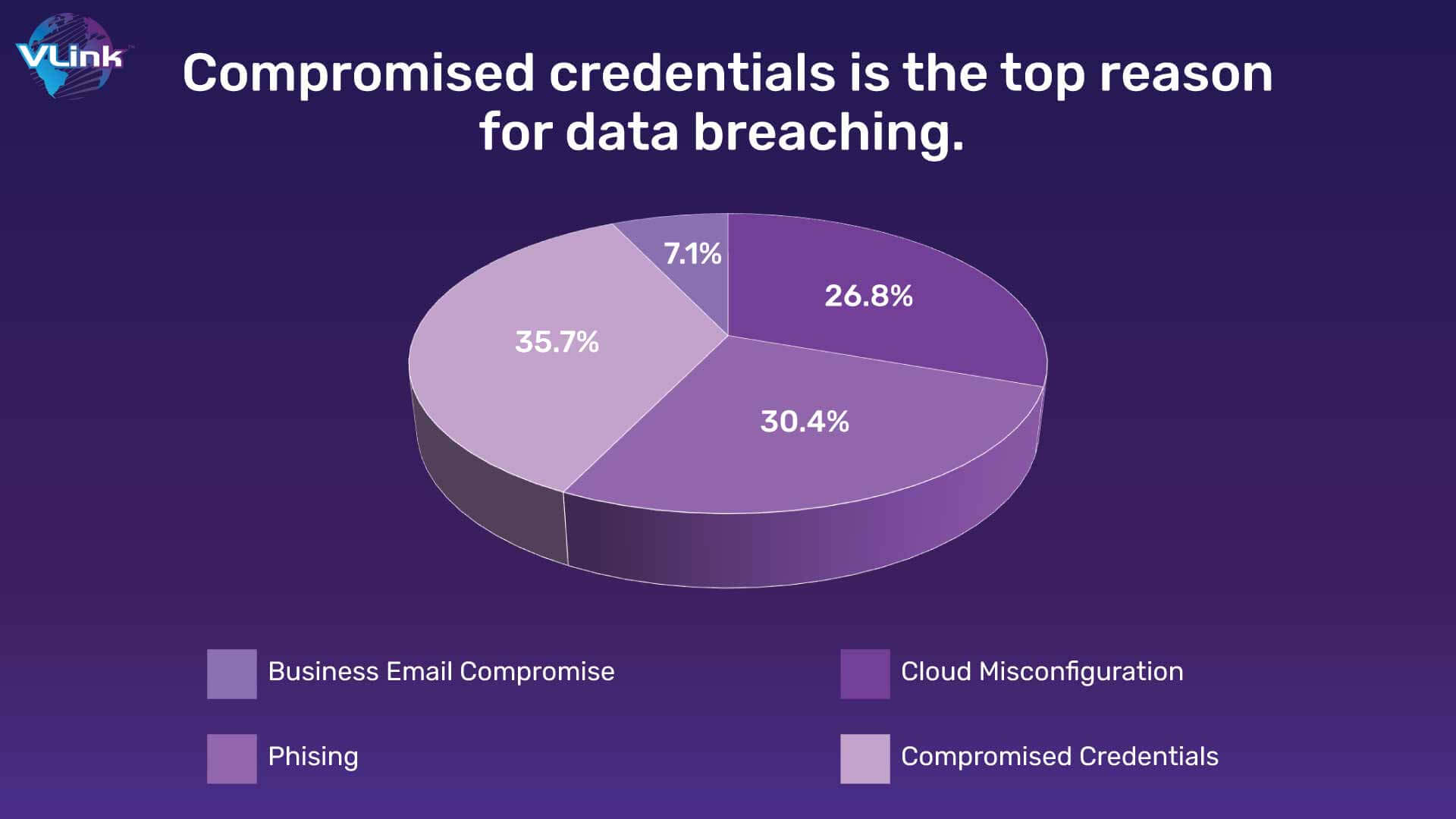 Security risks increase with the use of personal devices for accessing storage services such as One Drive and Dropbox, especially if you have an earlier version of your operating system. Insider threats are other aspects through which sensitive information can be compromised. It may be susceptible if data and passwords are stored in a simple text file that an attacker has access to.
Security risks increase with the use of personal devices for accessing storage services such as One Drive and Dropbox, especially if you have an earlier version of your operating system. Insider threats are other aspects through which sensitive information can be compromised. It may be susceptible if data and passwords are stored in a simple text file that an attacker has access to.
This factor is the riskiest thing for Cloud Security. Unauthorized access via unauthorized access controls and misuse of employee credentials is the biggest cloud security threat identified by 53% of respondents, according to a new cloud security spotlight report.
An unauthorized user is someone who has no valid permission to access enterprise information, networks, endpoints, devices, or applications. It is good news that, in conjunction with access management policies, security solutions can be applied to address poor control of access.
How VLink can secure your cloud data management
With the transition to cloud computing, businesses need much more flexibility and scale to be able to compete against a volatile business environment. You should also remember, if you do not apply security best practices to cloud migration, it may expose your company to safety risks.
Do not allow it to happen to you. You should act immediately to prevent them from occurring in the initial attempt! VLink has a team of professionals who know how to develop and deploy trending cloud solutions and applications.
We have a tech stack of cutting-edge technologies like AI and big data, which will enable automation for your business. Just share your business idea and our cloud development team will work with agility to provide business-oriented solutions.
Frequently Asked Questions
In the area of cloud security, different aspects have a key role in maintaining an appropriate and efficient posture. As important as all these aspects are, protection of personal data is one aspect which stands out. The data of any organization is the lifeblood, and ensuring their confidentiality, integrity and availability are crucial to its success.
All data protection methods applicable to cloud computing shall be authentication and identification, access control, encryption, secure deletion, integrity checking as well as data masking.
The set of security controls protecting cloud environments from vulnerabilities and reducing the impact of a bad attack is called Cloud Security Control. In any cloud computing strategy, security controls are a central element.







